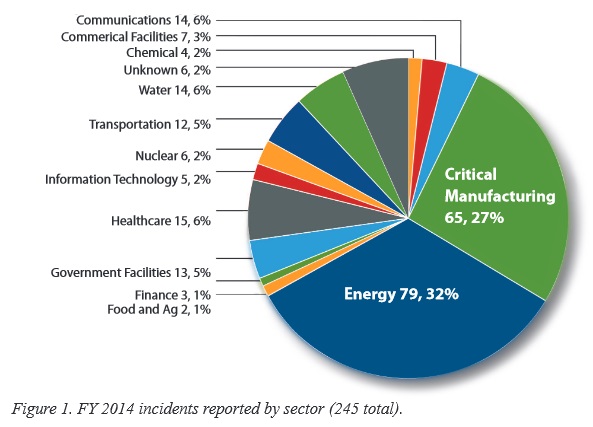
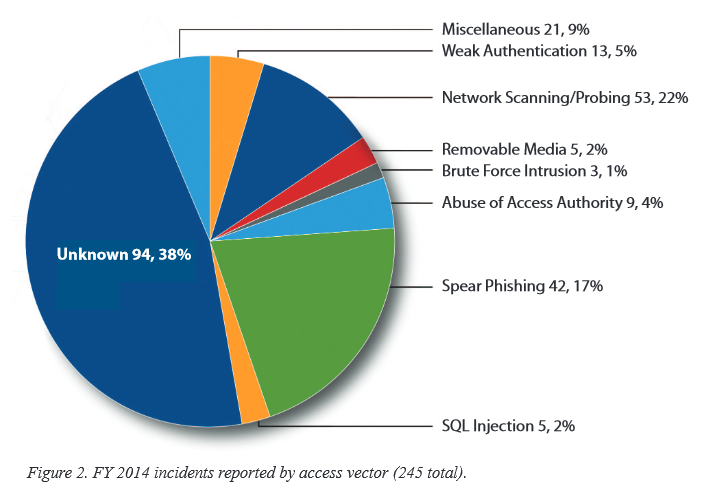
Washington, DC. March 12, 2015 — A report issued today by the US Department for Homeland Security says that in 2014 the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) responded to 245 incidents reported by asset owners and industry partners.
The energy sector, says Jeremy Cowan, led all others again in 2014 with 79 reported incidents, followed by manufacturing at 65 and worryingly healthcare at 15 reported incidents. ICS-CERT’s continuing partnership with the Energy sector reportedly provides many opportunities to share information and collaborate on incident response efforts.
Also noteworthy in 2014 were the incidents reported by the Critical Manufacturing sector, some of which were from control systems equipment manufacturers. The ICS vendor community may be a target for sophisticated threat actors for a variety of reasons, including economic espionage and reconnaissance. Of the total number of incidents reported to ICS-CERT, roughly 55% involved advanced persistent threats (APT) or sophisticated actors.
Other actor types included hacktivists, insider threats, and criminals. In many cases, the threat actors were unknown due to a lack of attributional data, says the US Department. The scope of incidents encompassed a vast range of threats and observed methods for attempting to gain access to both business and control systems infrastructure, including but not limited to the following:
- Unauthorised access and exploitation of Internet facing ICS/Supervisory Control and Data Acquisition (SCADA) devices
- Exploitation of zero-day vulnerabilities in control system devices and software
- Malware infections within air-gapped control system networks
- SQL injection via exploitation of web application vulnerabilities
- Network scanning and probing
- Lateral movement between network zones
- Targeted spear-phishing campaigns
- Strategic web site compromises (a.k.a., watering hole attacks.)
The majority of incidents were categorised as having an “unknown” access vector. In these instances, the organisation was confirmed to be compromised; however, forensic evidence did not point to a method used for intrusion because of a lack of detection and monitoring capabilities within the compromised network.
Rob Miller, security consultant at MWR InfoSecurity, tells M2M Now, “Many organisations we work with are taking these reports very seriously. The report shows that the rate of new vulnerabilities being discovered in ICS equipment has remained steady for the last four years. ICS operators cannot therefore rely on vendors taking care of their security for them.
“Organisations may feel that their ICS systems are beyond the reach of attackers, but attacks like those against the Norwegian oil sector last year have demonstrated these assumptions to be false. ICS, far from being an air-gapped, proprietary system, is now often integrated to our IT networks as companies strive to improve performance and reduce costs. This can be done without impacting security, but only if security is considered during its design.”
Miller concludes, “Ultimately, better ICS security comes from not only controlling the borders of an ICS system, but by also introducing the ability to monitor and detect attacks, and through training of staff to respond appropriately.”
You can comment on this article below, or via Twitter: @jcm2m OR @m2mnow