Critical national infrastructure firms have been advised by security experts Symantec to check their networks after the discovery of a new attack, codenamed Dragonfly. Also known as Energetic Bear, Dragonfly is said to be capable of doing damage to utilities on the same scale as Stuxnet.
A continuing cyberespionage campaign against various targets, mainly in the energy sector, is reported to have given attackers the ability to mount sabotage operations against companies, Jeremy Cowan reports. The attackers, known to Symantec as Dragonfly, have already compromised a number of strategically important organisations worldwide for industrial espionage. If they continue to use the sabotage capabilities open to them, says Symantec, they could damage or disrupt energy supplies in affected countries.
Among Dragonfly’s targets are energy grid operators, major electricity generating firms, petroleum pipeline operators, and energy industry equipment providers. Most of the enterprises falling victim to these attacks are in the United States, Spain, France, Italy, Germany, Turkey, and Poland.
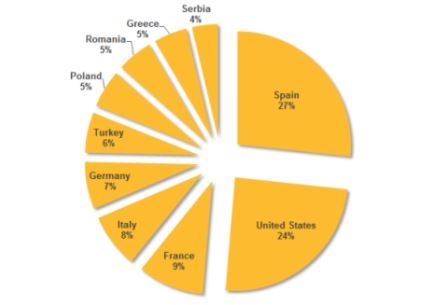
Figure. Top 10 countries by active infections (where attackers
stole information from infected computers)
Well resourced hacking campaign
With a range of malware tools at its disposal and having launched attacks through a number of different vectors, the Dragonfly group is described as “well resourced”. It has compromised a number of industrial control system (ICS) equipment providers, infecting their software with a remote access-type Trojan. This has caused companies to install the malware when downloading software updates for computers running ICS equipment. Said a spokesman for Symantec, “These infections not only gave the attackers a beachhead in the targeted organisations’ networks, but also gave them the means to mount sabotage operations against infected ICS computers.”
Symantec added: “This campaign follows in the footsteps of Stuxnet, which was the first known major malware campaign to target ICS systems. While Stuxnet was narrowly targeted at the Iranian nuclear programme and had sabotage as its primary goal, Dragonfly appears to have a broader focus with espionage and persistent access as its current objective with sabotage as an optional capability if required. In addition to compromising ICS software, Dragonfly has used spam email campaigns and ‘watering hole’ attacks to infect targeted organisations. The group has used two main malware tools: Backdoor.Oldrea and Trojan.Karagany. The former appears to be a custom piece of malware, either written by or for the attackers.
Symantec has already notified affected victims and relevant national authorities, such as Computer Emergency Response Centers (CERTs) that handle and respond to internet security incidents.
Dragonfly may be state-sponsored
The Dragonfly group, appears to have been in operation since at least 2011 and initially targeted defence and aviation companies in the US and Canada before shifting its focus to US and European energy firms in early 2013. The campaign against the European and American energy sector soon expanded in scope, and reportedly bears the hallmarks in high technical capability of a state-sponsored operation.
Commenting on the attacks, director of security research, Tom Cross at network intelligence firm Lancope said: “This is an attack that is directly targeted at western industrial control systems and is suspected to be of Russian origin. Although we don’t know the motive behind these attacks, the purpose of controlling these systems may be to disable them at some point in the future. Russia has used cyberattacks in conjunction with conventional warfare in the past, such as the 2008 conflict between Russia and Georgia. Therefore, it is alarming to hear that a malware variant suspected of having Russian origin has been directly targeted at industrial infrastructure.”
Symantec Corporation (NASDAQ: SYMC) is an information protection expert. Founded in April 1982, Symantec is a Fortune 500 company that operates one of the largest global data intelligence networks The company has provided security, back-up and availability solutions for businesses storing, accessing and sharing information.
Lancope, Inc. is a provider of network visibility and security intelligence to defend enterprises against today’s threats. By collecting and analysing NetFlow, IPFIX and other types of flow data, Lancope’s StealthWatch® System is said to help organisations quickly detect a wide range of attacks.











