How to protect the patient’s data and identity in an increasingly digital world. Best practice advice from the Personal Connected Healthcare Alliance.
Remote health monitoring and Electronic Health Record (EHR) technologies are under development worldwide to improve the quality and safety of healthcare coordination and public health – while still ensuring the privacy and security of patient health information. Interoperability and scalability enable cost savings and are thus fundamental to affordable healthcare coordination.
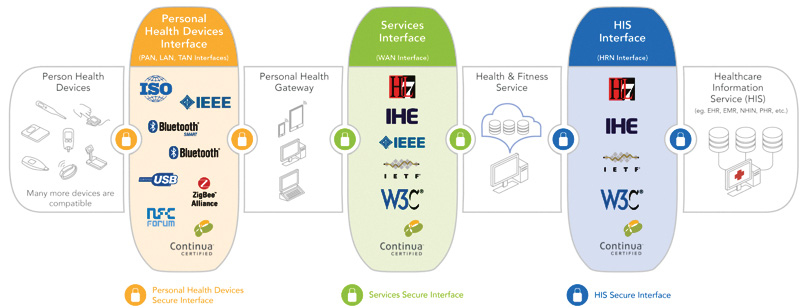
The remote monitoring and EHR ecosystem includes end-users taking measurements using state-of-the-art medical & fitness sensors, gateways to communicate these measurements over a network to health & fitness providers, and finally to health information services to allow access to patient information by a clinician.
The Personal Connected Health Alliance (PCHA) is a leading organisation convening, constraining and advocating global technology standards to advise developers of end-to-end interoperable solutions for personal connected health. It publishes the Continua Design Guidelines that clearly define interoperable interfaces that enable the secure flow of medical data among sensors, gateways, and end services, removing ambiguity in underlying healthcare standards and ensuring consistent implementation through product certification.
The Continua Design Guidelines implements a Personal Health Devices Interface centered around or defined by the IEEE 11073 Personal Health Device (PHD) family of standards for data format and exchange between the sensor and the gateway. It defines a Services Interface centered around or defined by the Integrating the Healthcare Enterprise (IHE) PCD-01 Transaction to move data between a Personal Health Gateway and Health & Fitness Services.
A Health Information Service Interface is centered around or defined by the Health Level 7 International (HL7)-based Personal Health Monitoring Report (PHMR) to move information between a Health and Fitness Service and Healthcare Information Service provider (e.g. EHR). End-to-end security and privacy are addressed through a combination of identity management, consent management and enforcement, entity authentication, confidentiality, integrity and authentication, non-repudiation of origin, and auditing.
Personal Health Devices Interface
The IEEE 11073 Personal Health Device family of standards was developed by the IEEE to specifically address the interoperability of personally owned medical or health devices (e.g. thermometers and blood pressure monitors) with an emphasis on personal use and a more simple communications model. This family of standards ensures that the user of the data knows exactly what was measured where, when, and how, and that this critical information is not lost as it is transported from the sensor, across the gateway and, ultimately, to the electronic health record system.
The Continua Design Guidelines support the secure transmission of IEEE 11073 standards-based personal health data from a Personal Health Device (e.g. sensor) to the Personal Health Gateway over a variety of networking transports including USB, ZigBee, NFC, Bluetooth and Bluetooth Low Energy (LE).
Data confidentiality and integrity across the Personal Health Devices Interface is achieved via the underlying network communication technology associated with each device. For example, a PHD interface employing the ZigBee standard would implement security mechanisms per the ZigBee Healthcare Profile. The Bluetooth LE transport would utilise LE security mechanisms such as Passkey Entry Pairing, association models, key generation, and encryption.
Data Authentication, Authorisation, Integrity, Confidentiality, Privacy, Availability, Accessibility and Traceability may be incorporated into the IEEE 11073 device specialisations and would be supported in the Continua Design Guidelines.
Services Interface
The Services Interface allows the uploading of the data gathered at the patient point of care to include personal health device observations, the exchange of questionnaires and responses, and the management of consent directives over a wide area network via HTTP and RESTful interfaces. The design guidelines ensure interoperability by constraining the IHE profile specifications and the HL7 messaging standards, providing implementation guidance and then independent interface certification to ensure adherence to the correct guidelines. For the Services Interface, security is achieved through confidentiality, integrity and service authentication, consent management, consent enforcement, auditing, and entity authentication as outlined below.
Confidentiality, Integrity and Service Authentication employs web services layer security between the gateway and EHR via the Web Services Interoperability Basic Security Profile. This profile provides interoperability guidance for core web service specifications such as SOAP.
Consent management is achieved via the HL7 CDA® Release 2 Consent Directive. This directive documents a bilateral agreement between the patient and an individual or organisation, which grants or withholds authorisation to access individually identifiable health information about the patient. HL7 has produced a draft standard for trial use for implementing consent directives using CDA Release 2.
Consent Enforcement is realised by implementing the World Wide Web Consortium’s (W3C) eXtensible Markup Language (XML) Encryption Standard to enable enforcement of patient consent by encrypting the measurement or questionnaire payload in addition to using point-to-point link security. This enables both the sender and the receiver of the payload to control access to the payload based on the consent policy. In the case of the transport protocol using hData over HTTP, consent enforcement is enabled through the use of IHE DEN profile.
Auditing is accomplished via IHE’s Audit Trail and Node Authentication (ATNA) Integration Profile, creating a secured domain by ensuring that communicating entities are authenticated by local systems (e.g., X.509) before allowing network access.
Entity Authentication constrain the Web Services (WS) Security profile from the WS-Interoperability Basic Security Profile by using only the WS-Security Header with the SAML 2.0 assertion as security token and allowing the use of any other token for providing the identity information, including OAuth. Assertion is utilised via SAML 2.0 within HTTP/SOAP uploads and OAuth access tokens are used in REST/hData uploads.
Health Information
Services Interface
The Health Information Services Interface provides for the electronic exchange of health records employing an HL7-based PHMR. Continua worked with HL7 to develop and define the PHMR to aggregate and deliver personal healthcare monitoring information to electronic medical record systems, including the representation of measurements captured by personal health devices. Continua is currently updating the HL7 PHMR specification, turning the Draft Standards for Trial Use (DSTU) into a final normative specification. Security is achieved through confidentiality, integrity and authentication, entity authentication, identity management, consent management, consent enforcement, non-repudiation of origin, and auditing as outlined below.
Confidentiality, Integrity and Authentication employs transport layer security as specified in IHE’s Cross Enterprise Document Reliable Interchange (XDR) profile for direct communications. For indirect communications via the IHE Cross Enterprise Document Media Interchange (XDM) profile, the exported file is delivered via email using S/MIME to ensure security.
Entity Authentication is achieved via the IHE Cross-Enterprise User Assertion Profile (XUA), to provide a means to communicate claims about the identity of an authenticated principal (e.g., user, application, system) in transactions that cross enterprise boundaries. The IHE Cross-Enterprise User Assertion Profile – Attribute Extension (XUA++), extends the XUA profile with options that enable access controls on the service side (consumer of the data).
Identity Management is realised via IHE’s Patient Identity Feed Transaction to communicate patient identification and demographic data, IHE Patient Identifier Cross-Reference HL7 Version 3 (PIXV3) to provide cross-referencing of patient identifiers from multiple Patient Identifier Domains (systems that share a common identification scheme and issuing authority for patient identifiers), and Patient Demographics Query HL7 Version 3 (PDQV3) to allow for multiple distributed applications to query a patient information server for a list of patients, based on user-defined search criteria, and retrieve a patient’s demographic information directly into the application.
Consent Management is accomplished via the HL7 CDA Release 2 Consent Directive that, as explained earlier, grants or withholds authorisation to access individually identifiable health information about the patient.
Consent Enforcement is achieved via the IHE Document Encryption Profile which provides a means to encrypt health documents independent of particular transport, healthcare application, or document type, thereby supporting end-to-end confidentiality in heterogeneous or unanticipated workflows.
Non-Repudiation of Origin, which is the assurance that someone cannot deny something, such as the receipt of a message or the authenticity of a statement or contract, is realised via the IHE Document Digital Signature profile that specifies the use of digital signatures for documents that are shared between organisations.
Auditing, similar to the Services Interface, is accomplished via IHE’s Audit Trail and Node Authentication Integration Profile.
The PCHA’s Continua Design Guidelines is the only international initiative to establish a secure end-to-end ICT framework for personal connected health and care with open standards. It is the implementation specifics defined by these Continua Design Guidelines, and the independent certification of each vendor’s implementation, that helps to ensure secure and authentic interoperability from remote personal healthcare devices/sensors to personal health gateways and on to electronic health records systems.
For further information, white papers are available on the Personal Connected Health Alliance website.
Thom Erickson is member, board of directors, Personal Connected Health Alliance (PCHA) and VP, product management, Qualcomm Technologies.