It should come as no surprise that Supervisory Control and Data Acquisition (SCADA) and Industrial Control Systems (ICS) that control key functions in critical infrastructure are especially at risk of cyber attack. If saboteurs manage to compromise critical infrastructure services, a country’s economy and military defenses can be severely hampered.
In addition, since organisations that operate critical infrastructure often own valuable intellectual property, this information can be a target for foreign state actors trying to steal intellectual property to advance their economies or to win competitive bids, says Deborah Galea, manager, OPSWAT.
So what is the current state of SCADA Security? In the past year we have seen some disturbing news that highlights the growing risk of SCADA attacks:
- December 2014 – SCADA attack causes physical damage: In late 2014, an unnamed German Steel Mill suffered extensive damage from a cyber attack. The attackers were able to disrupt the control system and prevent a blast furnace from being shut down, resulting in ‘massive’ damage.
- March 2015 – Energy sector hit the hardest: A report by the US Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) found that it received 245 cyber incident reports from asset owners and industry partners in the fiscal year of 2014. The largest number of these incidents occurred in the energy sector with 79 incidents.
- April 2015 – Number of SCADA attacks doubles: According to the 2015 Dell Security Annual Threat Report, SCADA attacks are on the rise. The report found that in 2014, the number of attacks on SCADA systems doubled compared to the previous year. Most of these attacks occurred in Finland, the United Kingdom, and the United States. This is probably due to the fact that in these countries SCADA systems are more likely to be connected to the internet.
- October 2015 – Nuclear industry especially at risk: Chatham House, a UK think-tank, reported that the risk of a cyber attack on nuclear infrastructure is growing. The trend towards the digitisation of SCADA systems is increasing the vulnerability of nuclear facilities, and many are inadequately prepared. Even where facilities are air-gapped, this safeguard can be breached with nothing more than a flash drive.
- November 2015 – SCADA Security priority for US military: At the recent CyberCon 2015 conference, LTG Alan Lynn, DISA (Defense Information Systems Agency) director, said: “We recognise the enemy will use the Internet to recruit, to take down SCADA systems. In short, we expect a cyberattack as a prelude to war.”
How can SCADA Security be improved?
It is clear that SCADA security needs to be improved. The most common method used to protect SCADA and ICS systems is ‘air-gapping’ the control systems and completely disconnecting them from the internet and the corporate network. This has the advantage that attackers are not able to access the system from the outside, but also severely hampers productivity. In addition, this creates a new attack vector in the form of portable media. Since portable media such as USB devices, CDs and DVDs are often the only way to transfer data into a secure facility, they become the new attack vector for hackers. Not only can USB sticks contain malware, they can also be booby-trapped. Microsoft recently revealed a vulnerability in Windows which could allow an attacker to execute malicious code from a booby-trapped USB. Given these problems, how can SCADA Security be improved?
The following three technologies can be used to bolster the security in SCADA and ICS systems:
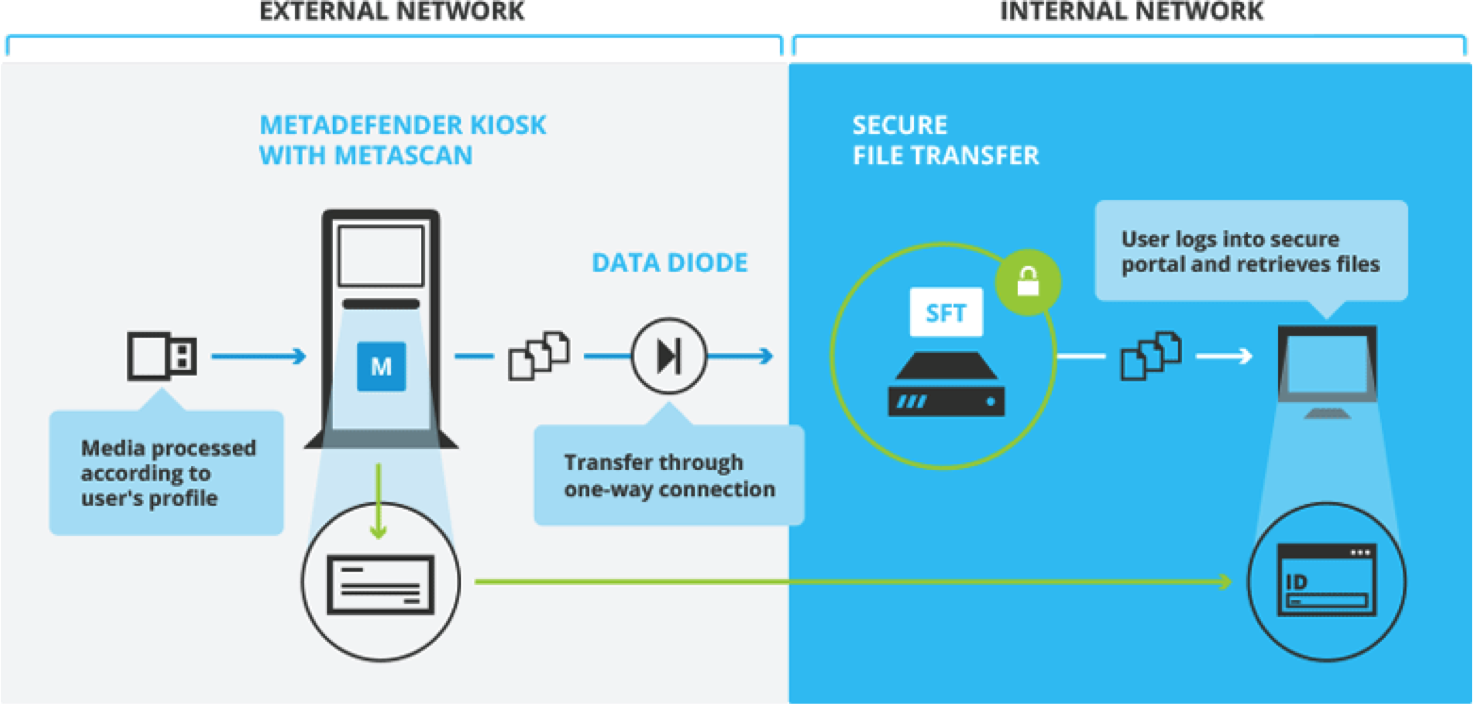
- Portable Media Security: By extensively scanning any portable media such as USB sticks, CDs and DVDs for malware before they are allowed to connect to the secure network, as well as applying security policies to limit allowed file types and media devices, the portable media attack vector can be significantly minimised.
- Data Diode: By making use of a data diode or one-way gateway to connect lower security networks to higher security networks, data transfer is only possible either in or out of the secure network, not vice versa. This significantly improves productivity by providing limited connectivity, while still maintaining the integrity of the secure network since data can only be transferred in one direction.
- Secure File Transfer: Secure file transfer can be used to safely send data into the secure network. For instance, after scanning portable media for any malware, the files can be sent into the secure network with secure file transfer, avoiding the need to bring portable media into the secure area. This not only improves productivity but also avoids the risk of booby-trapped USB devices being connected to the secure network.

There is no doubt that in 2016 cyber security will be one of the top concerns for SCADA and ICS operators. By ensuring that security is planned into the system from the beginning rather than being added on as an afterthought, SCADA security can be strengthened and attacks can be countered.
The author of this blog is Deborah Galea, manager, OPSWAT.
Comment on this article below or via Twitter: @IoTNow_ OR @jcIoTnow