Applications are created and deployed in OT domains. They operate in IT domains, alongside or incorporated in mainstream business processes like ERP. Seamless integration between these disparate worlds is a mandatory IoT requirement.
The Internet of Things (IoT) comprises numerous vertical sectors, one of which is Enterprise IoT. IoT solutions are based on M2M technology, which is why applications are created and deployed in an Operational Technology (OT) domain. Gartner defines OT as hardware and software that detects or causes a change through the direct monitoring and/or control of physical devices, processes and events in the enterprise. That is what M2M does, says, Bob Emmerson independent M2M writer and analyst.
These applications operate in enterprise environments, which are Information Technology (IT) domains. The technologies that are employed are well established and they are radically different to those of the OT domain. This means that there is a communications barrier, one that has to be dissolved in order to deliver the business case for implementing an IoT solution. It’s a case based on the proven ability to realise tangible benefits, e.g. boost enterprise-wide operational efficiency, enhance customer service, open up new business opportunities, and increase agility. Enterprises that fail to realise these benefits could find themselves falling behind the IoT curve.
Dissolving the barrier
Data is acquired in one domain and used (processed) in another. Dissolving the barrier that divides them is realised by decoupling (separating) acquisition from usage. That is not needed in M2M solutions as they are physically linked: they transfer from one device directly to a single application. It is required for IoT solutions since the concept is predicated on the ability to allow data to be shared between apps, enable interaction and interoperability. In enterprise environments it’s a given: something that ICT professionals take for granted.
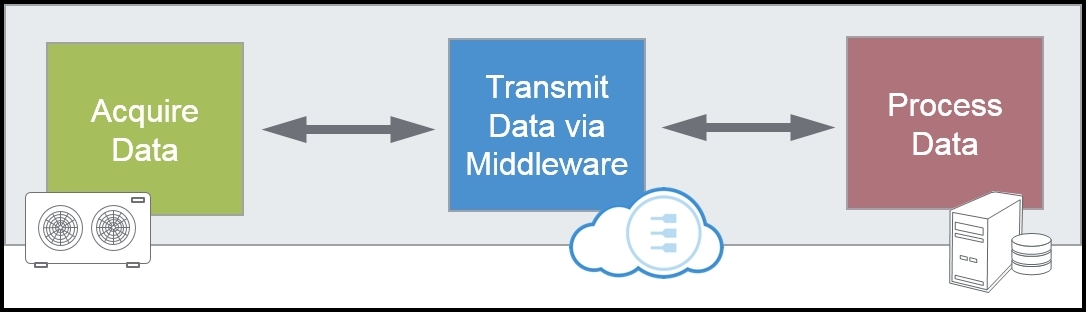
Data acquisition and data processing are decoupled by middleware, which is normally located in the Cloud. You can think of it as software glue. In computing environments middleware supports complex, distributed business software applications and similar functionality is required for the IoT. In that environment it enables end-to-end solutions to be deployed in a virtual architecture, in which virtual circuit links appear to function as physical links between data sources and data destinations.
What else happens when the barrier goes?
Middleware located in the Cloud enables a South-North flow of data: from devices to business applications, but that is only part of the integration challenge. When the barrier is dissolved the OT domains will appear to be seamless extensions to the enterprise networks, which means that seamless management of thousands to millions of devices is needed. Therefore, the flow has to be bidirectional, as shown in the above figure.
Different vendors will implement this facility in different ways. Eurotech simplifies the remote management of connected devices by using a single transport protocol, MQTT, over secure cloud services. Once devices are deployed, a software framework lets users connect, configure, and manage devices throughout their life cycles, from deployment to maintenance to retirement.
The need to manage lots of new things (devices) is linked to the need to employ a new security model. Gartner lists security as the #1 challenge to making the IoT a reality. IoT devices must make real-time, bi-directional connections to the Internet and securing that type of communication is challenging. Whereas security protocols and best practices for servers, personal computers, and smartphones are well understood and broadly adopted, security for IoT devices is nascent and the requirements are not widely understood.
This is a wide-ranging, multi-faceted topic; for example, a robust security model needs to operate over the many different communication technologies involved in end-to-end device to enterprise solutions. But an end-to-end security solution needs to encapsulate the complexity of the value chain, i.e. it needs to address issues in the individual elements: device hardware, device application and the communications infrastructure. In addition, there is a clear need to shift the primary burden of securing the new IoT devices from the hardware manufacturers into the network layer, which is more flexible and robust and it also enables security updates. PubNub has published an informative white paper on this subject: “A New Approach to IoT Security”.
Security is a moving target, so it is advisable to have an independent certified security firm to perform remote vulnerability assessments at regular intervals, e.g. every quarter, or when there is a major change in the infrastructure and the environment.
The author of this blog is the independent M2M writer and analyst, Bob Emmerson.
He can be contacted at: bob.emmerson@melisgs.nl
Comment on this article below or via Twitter: @IoTNow_ OR @jcIoTnow










