The potential of the Internet of Things is no secret: Gartner predicts 20.8 billion things will be connected by 2020. Others say that number could be as high as 50 billion. But connecting technologies in new ways and deploying them in new cyber-physical environments creates countless new security threats.
A recent 2015 cybersecurity report from AT&T noted a 458% increase in IoT vulnerability scans of devices, says Lancen LaChance of GlobalSign. We can see here that IoT devices extend the attack area in an ecosystem. To compound the concern, trends are also increasing for providers to leverage software-based mechanisms to enable features of their devices, leading to the question: How do you prevent counterfeiting and piracy of your product?
At the same time, IoT products are on the development fast track and manufacturers are rushing to create exciting new smart devices with user experience in mind, not necessarily security. So, what is the best approach for manufacturers to integrate security into their products from the outset? To help answer that, let’s first take a look at three security concerns that IoT developers need to address; authentication, privacy and integrity.
Authentication
The purpose of authentication is to prove that all entities are who (or what) they say they are. This ensures communications are delivered only to the intended recipient and that the recipient knows with certainty where the communication came from. In terms of IoT, authentication from devices to cloud services, users to devices, things to things, and in fact any entity to any other entity are all possible scenarios.
Privacy
There are a myriad of devices connecting to the IoT collecting sensitive data. IoT devices pose a threat to user privacy if manufacturers and service providers don’t include sufficient protections. It is critical for device manufacturers to ensure that information intended for a particular recipient cannot be intercepted and read by anyone (or anything) else. Enabling encryption is essential to ensuring privacy in the IoT.
Data integrity
Security technology can be used in IoT to protect the integrity of data by certifying the message sent to the recipient has not been changed or altered, either accidentally or maliciously. Some IoT ecosystems require devices to make decisions and act independently.
In these scenarios, both the value and risk are tied to the integrity of the data. For example, consider the impact of self-driving cars or the electric grid relying on spoofed data sources – the consequences could be catastrophic.
Introducing strong security elements
You can see the security needs of IoT call for a strong, proven approach to maintain security, trust and privacy in their ecosystem.
PKI is a foundational, proven, interoperable and standards-based technology that provides key information security capabilities, including authentication, privacy, and data integrity and is easily adapted to meet the velocity, variety and volume needs of the IoT. There are a wide variety of implementation approaches to bring PKI into your solution, but some of the most reliable ways incorporate cloud based PKI with device side cryptographic hardware, like TPMs or similar.
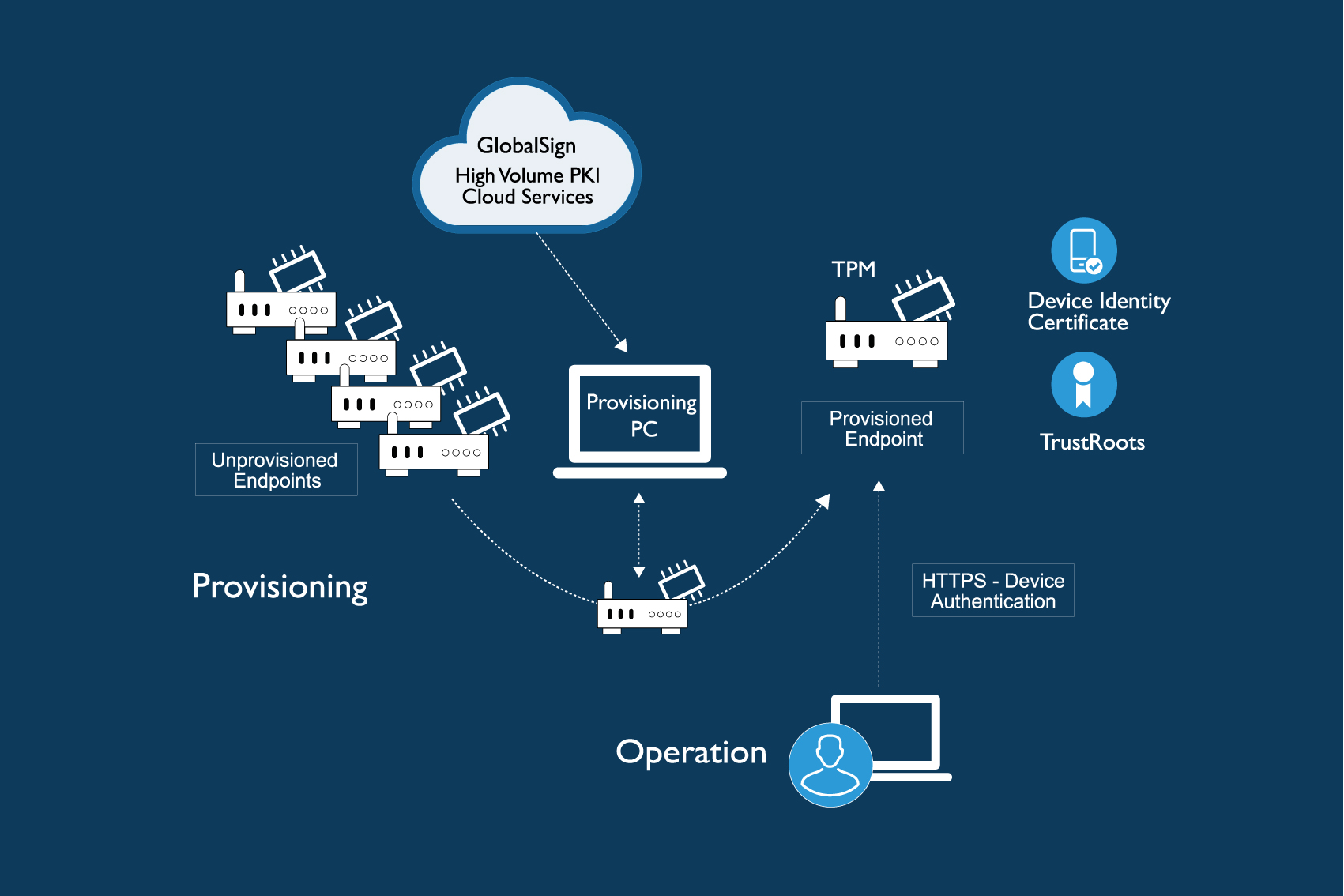 Enabling strong identities at the hardware level allows for protection against identity spoofing and key compromise which can endanger the whole interconnected system. If a change occurs then the entire ecosystem will know and administrators are able to respond accordingly.
Enabling strong identities at the hardware level allows for protection against identity spoofing and key compromise which can endanger the whole interconnected system. If a change occurs then the entire ecosystem will know and administrators are able to respond accordingly.
It is early enough to do IoT security right
The IoT is still very much in development and is creating exciting opportunities that manufacturers are trying more than ever to leverage, but security may be outside of their core competencies. However, it is imperative that IoT manufacturers know the implications their devices have on personal and corporate security and mitigate these security concerns during the development phase.
Retrofitting security into devices already in use is difficult, costly and a burden on the users. Implementing security in the early design phase supports manufacturers’ brand integrity and gives them a unique competitive advantage by allowing them to go to market with secure devices and improve user experiences faster.
The author of this blog is Lancen LaChance, vice president of IoT Solutions at GlobalSign and can be reached at Lancen.LaChance@globalsign.com
Comment on this article below or via Twitter: @IoTNow_ OR @jcIoTnow










