The Internet of Things (IoT) vision can become reality, enabling the large spectrum of opportunities the industry is imagining, only if it is designed with a security-centric framework. Security is the indispensable prerequisite for the development of the IoT. This sentiment is shared by the entire IoT community, from the IoT solution and technology providers to the adopters, from the research community to governments and regulators. However, that consensus often is not reflected in the status of IoT security development. In order to understand more about the current status and the issues behind that, Saverio Romeo, the principal analyst at Beecham Research, spoke to Rob Black, the senior director of product management at ThingWorx-PTC. Black has spent more than ten years in security, at Axeda and now PTC, focusing specifically on IoT security. Holding a Certified Information Systems Security Professional (CISSP) certification, he has experience and knowledge on the evolution of IoT security and on its future developments.
Saverio Romeo: Considering your long experience in the security market and, specifically, IoT security, can you give us an overview on the state of development of IoT security?
Rob Black: There are different levels of awareness and adoption of IoT security solutions. If we want to analyse those levels in an easy way, we could identify two main groups: consumer IoT security and enterprise IoT security. I would say that the understanding of security in consumer IoT products and solutions is immature. Attacks on various consumer connected devices show the vast spectrum of vulnerabilities and the inability of protecting against them so far. In contrast, the enterprise IoT security group shows more consciousness of the problem and, consequently, pays much more attention to introducing the right security approach in products and solutions. However, within this group, we can find different levels of adoption of IoT security. We have on one extreme organisations with very sophisticated approaches but on the other extreme, organisations with very similar attitudes to the consumer IoT security group.
SR: In the consumer IoT device space, where do you see the major problems and how should they be addressed?
RB: There is an important starting point for device makers which is that your device is not a stand-alone device, but interconnected with many other connected devices. Therefore, if not secured, it could represent the weak point that allows compromise of an entire network of devices. But, it could be affected by attacks on other devices with which it shares the same network. Therefore, the design of the device in all its components – panels, wiring, printed circuit boards (PCBs) and embedded electronics – should be taken into serious consideration from the ground-up design of the device, based on IoT security best practices and guidelines. On the other hand, it is also important to define easy-touse security configuration in order to be able to create trustful and confident relationships between the device and the consumer.
SR: Consumer IoT devices are managed through a mobile application which can be a weak entry point. What do you suggest for improving mobile application security?
RB: Weak security approaches at the mobile application level are unfortunately very common. The solution is not always easy, but it is available in the form of guidelines. The OWASP Top 10 Project is an excellent source to be used by mobile application developers.
SR: You have divided the enterprise side into two groups depending on their sophistication in regard to security, what is your definition of security sophistication?
RB: The sophistication of an IoT approach starts from being really mindful of the device or the solution. Being aware that security is not an addon, but a key part of the design from the inception of the idea is a key part of becoming sophisticated. The concept of security-by-design summarises that attitude. It then moves on to having an IoT security approach based on guidelines and best practices. We mentioned the OWASP Top 10 Project in the case of mobile applications but there are also others that are equally important. For example, it is important to have a secure software development lifecycle. We do not need to reinvent the wheel here, there are guidelines available for this. It is also important to test the solution and the product and also in this case, guidelines can help us. Finally, a lot of this is about hard work, attention and dedication.
SR: Which sectors show more sophisticated approaches?
RB: Sectors that have been historically highly regulated are showing more maturity than others moving along the lines discussed in the previous questions. Even within a sector there are differing levels of maturity. Some companies are compelled to focus on security while others see it as an opportunity to differentiate themselves. Therefore there are different security approaches taken by these various organisations.
 SR: Do you think the lack of skills in IoT security is also a barrier?
SR: Do you think the lack of skills in IoT security is also a barrier?
RB: Having security experts in the organisation is important. However, not all the organisations have those professionals. Small and mediumsized enterprises are those that suffer the most from the lack of security skills internally.
SR: In such scenarios, what does PTC offer?
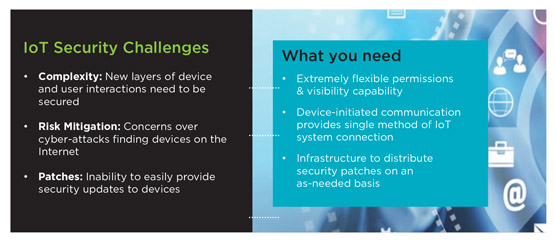
RB: PTC has a comprehensive security offer. Examples of security features are: authentication and authorisation, matrix multi-tenancy, security logging sub-system, encrypted data storage, supported application back-up strategy, protection of common vulnerabilities, backdoor protection, and support for transport layer security. However, there are three elements that make PTC more competitive in the market place: the Visibility and Permission Capability, the Device Initiated Communication Capability, and the Software Content Management Capability [see Figure 1].
SR: Can you tell us a bit more about the Visibility and Permission Capability?
RB: Non-administrative users and users groups have not had access to the platform until that has been granted by the administrator. The administrator can then design its own authentication and access models. Access control can be granted at a very granular level. For example, access can be granted only for a simple read and write operation on a thing property. There are also separate permission settings for design-time and for run-time. Both design-time and run-time permissions can be set for any entity in the system. This very fine and granular capability gives a lot of flexibility to the enterprise.
The framework behind that refined approach can be also applied to allow granular access and permission policies in multi-entity organisations such as a healthcare organisation composed of different hospitals. The approach called Matrix Multi-Tenancy enables assignment of a specific permission, called Visibility, to a specific entity. Therefore, the members of that entity are the only ones with the access granted. It is also possible to create a rule that enables access to specific things or a specific entity.
SR: Can you describe the Device Initiated Communication Capability?
RB: Each device has a pre-set parent server to communicate with. This means that the single method of IoT connection is the server and not the edge device. Therefore, instead of worrying about several entry points, the security concern should be ensured at server level.
SR: What about the Software Content Management Capability?
RB: Organisations cannot afford product recalls for security updates and reconfigurations. Security patches have to be distributed over the air. The Software Content Management Capability provides an infrastructure to distribute security patches whenever it is necessary.
SR: What is PTC’s business model?
RB: Our approach to market is primarily based on collaboration with channel partners. Certainly, we go direct to organisations, but, partnerships are increasingly important. Collaboration with solution providers is particularly important. The Internet of Things is impacting all sectors. Consequently, we increasingly operate in a variety of sectors and applications. The contribution of sector and solution specialists then becomes crucial to enable us to understand the context of the operations and the security approach to adopt.
SR: Are those partnerships involving forms of post-sales support?
RB: Certainly, yes, if it is necessary. We rely on the fact that our partners are specialists in the fields and therefore, the success rate is high. However, the collaboration can involve post-sale support. It is also important to remember that PTC offers customer support, cloud services and global post-service support.

Is principal analyst at
Beecham Research
SR: Robotics and artificial intelligence (AI) are becoming relevant topics in several IoT contexts. How do you see those in your daily experience and how will they affect IoT security?
RB: Today, most customers are not deploying AI solutions. They are more interested in advanced analytics such as predictive analytics. For those, the business value is more evident. We provide analytics capabilities. We enable integration with third party analytics packages. It is all part of our platform, therefore, thought-through from a security perspective as well.
Regarding robotics, we see an increasing use of robots, particularly in industrial settings. Our integration capabilities are very extensive. Therefore, our software is integrated in a diverse range of devices including robots.
Regarding the impact of AI and robots on the evolution of IoT security, probably, it is too early to say, but they are topics that needed to be observed and studied in order to identify a successful security approach.
SR: What are the future directions of IoT security in PTC’s opinion?

Senior director of
product management at
PTC
RB: The company has a strong commitment to continue the development of cutting-edge security technology in order to be able to face new threats to data, intellectual property and operations. We have a robust internal testing capability. Periodically, we test the platform at the network level and at the application level. We have internal and external security audits. We have a strong and skillful in-house team. We continue collaborating with solution providers and we learn from those collaborations but, probably, most importantly, our development process is based on secure software development best practices. That includes: risk assessment development in different iterations in order to have a clear view of the situation all through the operations; security requirement definition at the inception of the project and during the project; formal design reviews at the end of the design phase to ensure that security requirements have been satisfied; and security code reviews run during the development in order to verify that the code has been produced based on guidelines and best practices. Strictly following this approach will enable us to be always at the cutting-edge of the platform security offerings in the market place.
SR: What is your conclusive suggestion for IoT adopters in terms of how they should face security issues?
RB: As I said previously, security is also a lot of hard work, but there is a lot of help and knowledge out there. That is in the form of best practices and guidelines. It is also important to have the right partner that meets the security requirements and is able to respond to security challenges. PTC offers a very comprehensive security solution tackling key issues, such as complexity, risk mitigation and software patches, among others, in a strong way.










