The brand new concept of “Interoperable – Simple – Secure” solution of the IQRF technology, a Wireless Platform for IoT, was presented in the end of the 2016. Now, it is being fulfilled by new versions of the OS v4.00 and the DPA protocol v3.00 bringing higher safety of wireless communication, security of transferred data and higher comfort for users. Interoperability of the whole IQRF Ecosystem is being presented via solutions and IoT applications by the IQRF Alliance members on a daily basis.
“Every wireless system is exposed to potential OTA attacks. But IQRF OS v4.00 brings ultimate security based on industrial standards. Security in IQRF does not mean just an encryption but a complex approach to avoid potential vulnerabilities,” explained CEO of MICRORISC, inventor of the IQRF technology, Dr. Vladimir Sulc.
This complex approach consists of packets consistency checking, three levels of AES-128 encryption, and dynamic passwords and keys generation.
Packets consistency checking
Security starts at basic trust to received data. To avoid transmission errors and process valid data only, IQRF strictly checks all received packets against bit error failures using several block checksums. Additionally, complete packet is protected by standard IBM CRC-16.
Encryption
Sensitive data should be hidden for unauthorised users and systems. Encryption is a way how to protect such sensitive data. IQRF utilises AES-128 encryption, industrial standard for wireless communication. Besides hiding sensitive data, control data encryption increases consistency protection.
There are three different protections based on AES-128 encryption.
- Network communication protection
Protection of standard network communication is the most important as it continues during the whole system life. Protection is based on AES-128 encryption standard. Thus, only systems/users having valid network Password may join network communication and process data. To avoid wrong implementations all network communication has been forced to be encrypted automatically.
- Unauthorised access protection
Only authorised devices may join the network and only authorised users may have maintenance access to network devices. As communication during bonding and maintenance is encrypted by AES-128, only authorised devices and users with valid access Password are able to join the network or to maintain network devices. Sensitive data, such as network Passwords, exchanged encrypted during bonding, are well protected.
- User´s data protection
Besides protection of network communication there is an optional way to increase privacy by adding another encryption shield. It utilises AES-128 and user Key defined by the user to protect sensitive user’s data. This protection is fully under user’s control and may be used to add extra network protection or to hide sensitive data even from the IQRF platform as shown in the schematics below.
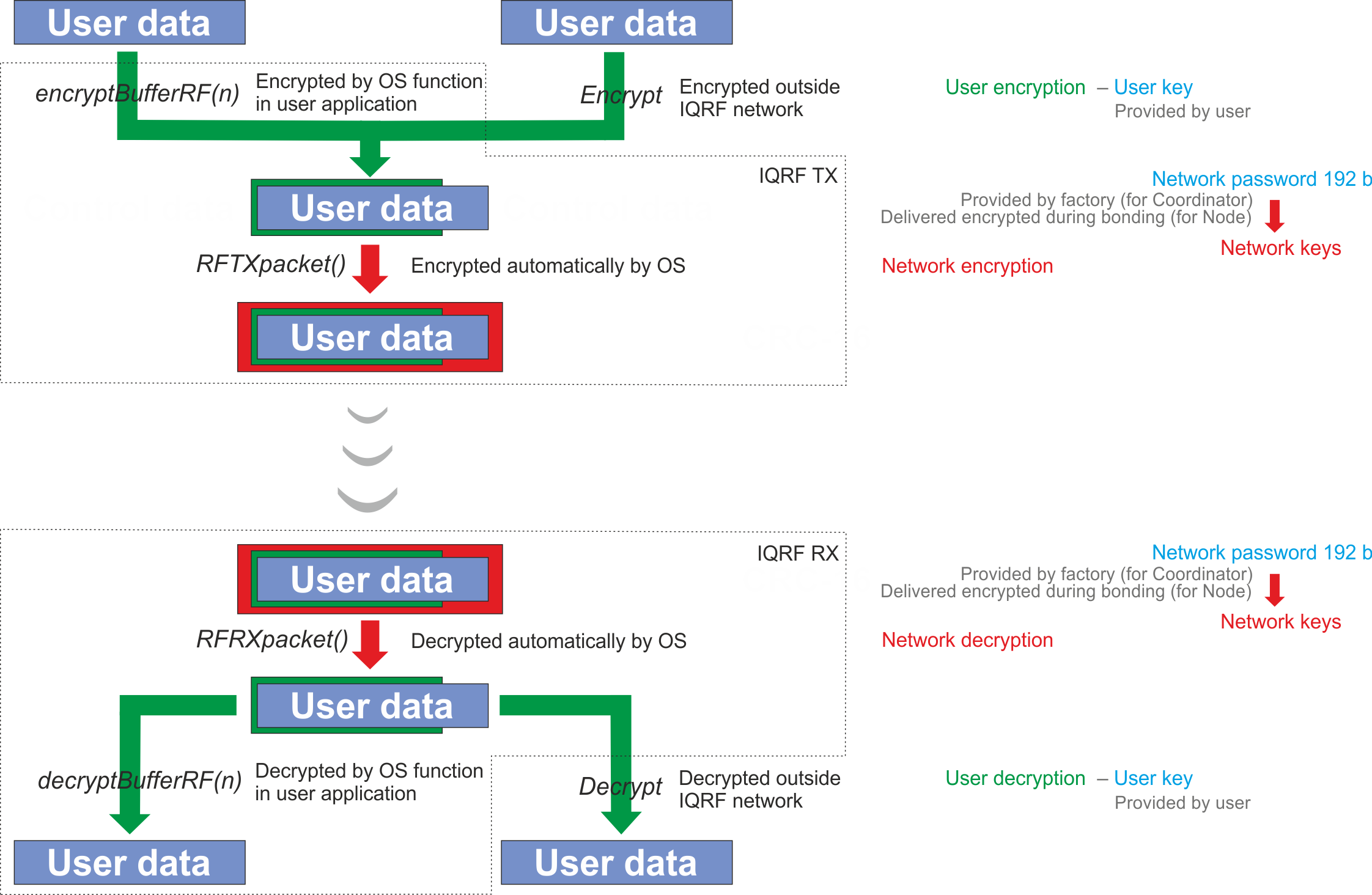
Password and Keys manipulation
Keys compromising is very frequent source of security problems. Therefore IQRF minimised and protected also manipulation with keys – network and access keys are not known during physical manipulation as they are generated from respective passwords. Network password is generated randomly with high entropy. The encrypted password is provided to devices that are joining the network during bonding.
Future upgrades
Threats coming in the future from more powerful attacking tools and from discovered vulnerabilities should be fixed. All IQRF software layers enable upgrades to keep system secure.
Further information:
- Register for a webinar to learn all about new features in the IQRF OS 4.0 30th March, 2017 – 13:00 to 14:30 CET.
- Detailed technical information is available here.
IQRF technology selected features:
- Ultimate security: based on industrial standards (AES-128)
- Extra low power: < 100 nA standby, 15 µA receiving in XLP mode
- Simple integration in a few weeks and simple control with DPA protocol (SPI, UART)
- Sub-GHz ISM bands: 433 / 868 / 916 MHz
- Range: 500 m with small PCB antenna
- Easily connectable to Arduino, Raspberry Pi, chipKIT etc.
Comment on this article below or via Twitter: @IoTNow_ OR @jcIoTnow










