IoT brings opportunities across the whole technology stack, making it an extremely high growth market. In Europe, IoT spending is expected to increase to $202 billion (€179.97 billion) in 2021 with spending projected to grow at 26.7% every year thereafter, especially with the arrival of 5G,
Not only have workforces moved to a more remote working environment, but many other industries are using IoT for a more connected experience across their businesses. For example, manufacturing and healthcare providers have increased IoT spending significantly over the past few years.
Although manufacturers were hit hard during the pandemic, the traditionally highly manual sector leveraged IoT to monitor and maintain equipment without a full team of staff, for tasks such as temperature and usage monitoring, says Jeff Costlow, CISO at ExtraHop. The healthcare industry implemented IoT in response to the pandemic, using the tech to help healthcare professionals improve the quality of life and care they offer patients through health monitoring solutions. This tech can also be used for home medical care, which will propel the industry to become the fastest-growing industry for IoT technology in the next few years.
But, as IoT expands across the globe to offer a more connected experience, security undoubtedly takes a hit. IoT technology is creating a broader attack surface, leaving businesses at risk to unknown vulnerabilities in their environments and exposing them to threats of attack.
The increasing attack surface of IoT devices
IoT devices are notoriously hard to monitor and secure. Today’s cybersecurity tools are far more advanced than the devices used on production lines, meaning many of them use legacy software which lack encryption capabilities. In addition, other IoT devices connect to the network infrequently, making them hard to track.
This means companies struggle to monitor and secure the increasing amount of devices used by businesses – a job many CISOs and security teams find frustrating. How are security experts expected to secure and patch IoT devices if they don’t know the device is there?
Additional threats arise when software updates need to be installed by individual employees who, in many cases, lack the skills to do so. This means important updates are not installed properly or when they are needed, leaving the network exposed.
In IT systems, end-point or logging technology can be deployed but with these small, unadvanced IoT devices, normal security telemetry can’t be. The lack of device inventory and vital updates to secure these connected devices cause a monitoring gap, leaving systems vulnerable and open to attacks.
IoT security nightmares
Without robust security and monitoring capabilities, insecure IoT devices open up the possibility of a cyber attack which could disrupt supply chains and cause chaos. This has been seen several times in 2021 with some of the ransomware attacks, such as those on the Colonial Pipeline, JBS and Kaseya, an IT software firm.
In the healthcare industry, a cyber attack could mean life or death for patients. Hospitals’ expansive networks are renowned for using legacy systems, which make them an easy target for attackers who know they’ll pay up to avoid the possible repercussions. This nightmare became reality in Germany, when the first human death from a ransomware attack happened as a hospital was targeted by unidentified hackers who are still unknown to this day.
Other examples of healthcare sector attacks include the infamous WannaCry attack in May 2017. WannaCry was the largest ransomware attack in history, and is still active today. The UK’s NHS was brought to a standstill for several days, and patient data was put at risk as trusts, care providers and general practitioner practices were all affected. This resulted in the cancellation of thousands of appointments and operations, and the relocation of emergency patients from targeted emergency centres. Most recently, the Irish Health Service fell victim to hackers threatening to sell the stolen data.
While it is unknown that these ransomware attacks involved IoT devices, there are attacks where unmanaged devices have caused cyber attacks. In August 2021, the Cybersecurity and Infrastructure Security Agency (CISA) and Mandiant, a threat intelligence firm, disclosed a critical vulnerability in ThroughTek. This vulnerability allowed attackers to access millions of IoT cameras to view and record live feeds and compromise credentials for further attacks. The vulnerability impacted an estimated 83 million recording devices, ranging from enterprise security cameras to smart baby monitors.
This discovery highlights the increasing challenges of IoT supply-chain security, which often demands immediate action by the software supplier, the manufacturer, and the end user to release patches and apply necessary software updates. Connected devices need to have the same cybersecurity as other IT systems to avoid exploitation which can have major consequences.
Monitor IoT with network detection and response
By looking at the evolving threat landscape and the rise in attacks which exploit IoT vulnerabilities, it’s clear organisations need to upgrade their security to protect themselves. More sophisticated network segmentation is needed, or a different approach, like Zero Trust, so that no asset is implicitly trusted.
At the same time, a device discovery plan should be in place for all IoT component producers to manage device inventory and containment. They also need to be able to gather deep forensics insights to investigate the cause of a threat and ensure it doesn’t happen again.
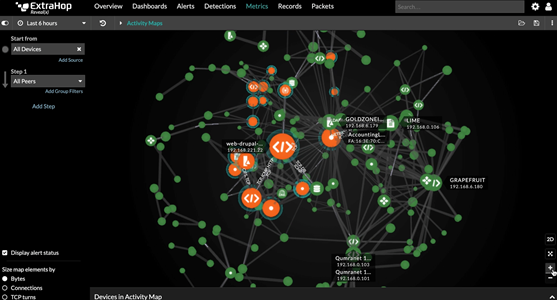
Connected devices require a more advanced network security tool, such as network detection and response (NDR), which shows organisations east/west movement and can display thorough device inventory taking the pressure off security teams.
It’s not enough to rely on endpoint or Endpoint Detection and Response (EDR) tools. Although these tools give an internal view, they can only monitor a device if they are able to be deployed on it. NDR solutions, however, can see everything on the network each device, traffic and activity.
It’s important for security teams to have an actionable plan in place to rapidly eradicate a vulnerability or risk from the business environment, leaning on deep forensic insight to help. These capabilities give teams everything they need at their fingertips to hunt, investigate and remediate threats quickly providing a full spectrum of response and streamlining the workflow.
From looking at the data, the growth of IoT is going to continue to explode – but so will sophisticated cyber attacks. Organisations need to ensure they are prepared by putting the right tools in place now to reduce response time when an attack inevitably hits. Being left in the dark is no longer an excuse.
The author is Jeff Costlow, CISO at ExtraHop.
Comment on this article below or via Twitter: @IoTNow_OR @jcIoTnow










