I. INTRODUCTION: A GLOBAL CHALLENGE
The IoT offers tremendous promise to consumers and businesses in applications across virtually every sector of the economy and throughout the world. Based on this promise, consumers, enterprises, and the government increasingly are adopting IoT technologies and embedding them into their homes, systems, and operations. 14.2 billion connected things will be in use this year, and that number is expected to grow to 25 billion by 2021.i The IoT is here, and it is continuing to grow worldwide.
Internet technologies, including the IoT, are fundamentally global in their supply, demand, development, and use. Security threats to—and emanating from—the IoT also are global, and they tend to have global impacts. Indeed, attacks on one country’s internet infrastructure need not originate from devices and networks in that country. Instead, compromised IoT devices in one country can be used by criminals in another to conduct attacks in yet another. Neither the internet nor the IoT stop, or even slow down, at national borders; nor do the security risks, threats, and challenges they pose.
The Mirai botnet attacks of late 2016 serve as a case in point—infected devices were disproportionately in South America and Southeast Asia, in particular Brazil, Columbia, and Vietnam, and yet the impact of Mirai was felt primarily in the United States and Europe.ii The attacks relied on infected home routers, network[1]enabled cameras, and digital video recorders,iii and one of the attacks brought many popular online services to a halt for the better part of a day.
For many policymakers, the Mirai attacks served as a watershed moment, demonstrating the impact that cyber criminals can have on the global internet by commandeering poorly secured IoT devices deployed all over the world. As the U.S. Secretaries of Commerce and Homeland Security later reported to the President, the Mirai attacks “highlighted the growing insecurities in—and threats from—consumer-grade IoT devices.
But these insecurities cannot be solved by regulatory fiat. The IoT’s complex global supply chains rely on a diverse market of developers, vendors, buyers, and users. To build high-quality, secure devices and still market them at reasonable prices, manufacturers must build at scale. Building on a region-by[1]region, country-by-country, or even state-by-state basis would markedly dampen the IoT’s promise—and hamper its security.
Put simply, global challenges require global solutions. A fractured approach must not emerge in the United States and abroad. Hundreds of different local legal jurisdictions and enforcement regimes with potentially differing requirements would add costs to manufacturing IoT devices that would harm the IoT’s potential without improving security. Instead, by making manufacturing less efficient and more The Internet of Things is Global – and an Internet of Secure Things Requires Global Solutions | 5 internet of secure things expensive, these requirements would divert resources from developing innovative security features and force manufacturers to build only to various minimum compliance obligations. In the end, devices would be more expensive and less secure.
A far better approach exists. Industry, in close collaboration with and supported by government experts dedicated to security innovation, can effect real positive change in IoT security at a global scale. An industry aligned on security can powerfully move—and keep moving—the global market toward security in a manner that jurisdictionally-limited and stagnant regulation cannot. Industry is actively working towards this goal—an Internet of Secure Things—through efforts like the ioXt Alliance.
The companies of the ioXt Alliance commit to take the next step beyond recommendations and best practices. We are developing rigorous security certification processes that will be enforced by real-world market requirements to radically change global marketplace demands for IoT security. Policy initiatives throughout the world should align with and promote this game-changing approach.
II. THE REGULATORY CHALLENGE: A FRACTURED APPROACH IS EMERGING
Some recent trends in the United States and abroad are alarming, even if well-intentioned. In the fall of 2018, California Governor Jerry Brown signed SB-327, the United States’ first connected device security law.vi Though the U.S. Federal Trade Commission for years has imposed a “reasonable security” expectation on manufacturers through enforcing its general consumer protection authority, beginning in January 2020, every connected device sold in California by law may require a unique password or a means to force new authentication credentials once the device is first used. Although presently a laudable best practice, codifying this requirement in statute does little to ensure that security continues to advance in the dynamic IoT ecosystem—in fact, it may actually handicap security by focusing too narrowly on passwords rather than other possibilities that security innovators are developing. Worse, it sets the stage for additional states to consider IoT security legislation—each state potentially with its own variation and enforced by its own regulators.
Interest in regulating device security abroad adds another layer of complexity and challenges. The European Union, for instance, has reached political agreement on a new comprehensive Cybersecurity Act that, among other things, will lead to setting certification schemes for ICT products, services, and processes.vii In turn, countries from other regions across the world could each establish their own versions of an IoT cybersecurity regulatory regime. Even slight differences among those regimes could create shockwaves to supply chains and product development processes, let alone if any jurisdictions take up more significant (and potentially conflicting) departures.
Should these trends continue, policymakers in the United States and abroad will be gambling with the future of the IoT and its promise—all for, at best, nominal gains in security, and, at worst, constraints on security advances.
III. A BETTER APPROACH: REAL INDUSTRY LEADERSHIP
Industry leadership and industry-driven solutions can better address security in the global IoT market, encouraging and enabling companies to design and build secure products to be sold and used anywhere across the world.
Industry leaders from various sub-sectors of the ICT economy already have demonstrated their commitment to a more secure IoT ecosystem. For instance:
• Approximately 40 companies, industry coalitions, and trade associations publicly participated in the effort led by the U.S. Departments of Commerce and Homeland Security to promote stakeholder action to stop botnets and other automated threats,viii and scores more have engaged with the National Institute of Standards and Technology’s (NIST’s) Cybersecurity for the Internet of Things (IoT) Program
• Associations representing a cross-section of the ICT ecosystem developed and published the Council to Secure the Digital Economy’s (CSDE’s) International Anti-Botnet Guide to recommend and promote security practices across the ecosystem, and have committed to updating the Guide on an annual basis
• Through CTIA, the wireless industry announced a new cybersecurity testing and certification program for cellular-connected IoT devices
• The Open Connectivity Foundation launched an initiative last year to promote IoT security by design and
• A coalition of companies that offer security products and services have developed threat mitigation profiles for DDoS attacks and botnet threats
These private sector-driven processes offer the flexibility product managers need to develop and design new innovative IoT products that take into account emerging customer needs. Further, such processes can account for the latest security threats and incorporate the latest security technologies and approaches—without waiting for an Act of Congress, a regulatory rulemaking process, or an update to a state law. These dynamic security approaches—as opposed to designing products in accordance with a series of differing statutory or regulatory compliance requirements—can best address global security challenges.
The industry’s work together is far from complete, however. This is why the forward-looking companies and organizations that make up the ioXt Alliance came together—to realize the potential of these many industry efforts by combining dynamic security solutions with real and reliable implementation of those solutions.
IV. THE INDUSTRY’S NEXT STEP: THE IOXT ALLIANCE
The ioXt Alliance was created to provide a vehicle for device manufacturers, technology vendors, technology alliances, standards organizations, and retailers to develop and align on security specifications, independent of the underlying connectivity technology. In turn, these specifications can be “enforced” by retailers when they request products for their sales channels, embedding security in the design and pre-market stages of the global IoT market. The ioXt Alliance also offers a forum for industry to collaborate with policymakers to develop responsive governance regimes that encourages this approach to IoT security. Thus, the ioXt Alliance aims to protect consumers and businesses across the United States and the world.
The ioXt Alliance is premised on implementing rigorous verification and certification processes that are real and that have teeth to ensure implementation of best practices. These processes will rely on security performance requirements that are validated technically, operationally, and contractually in the market. They also require pre-market validation for all devices, rather than simply post-hoc investigation and enforcement for some. Manufacturers that are part of the ioXt Alliance must ensure that their devices meet baseline performance requirements through testing that give consumers, businesses, and retailers confidence in our highly connected world.
Major manufacturers and organizations comprising the ioXt Alliance have committed to developing a secure IoT through implementation of the ioXt Security Pledge.
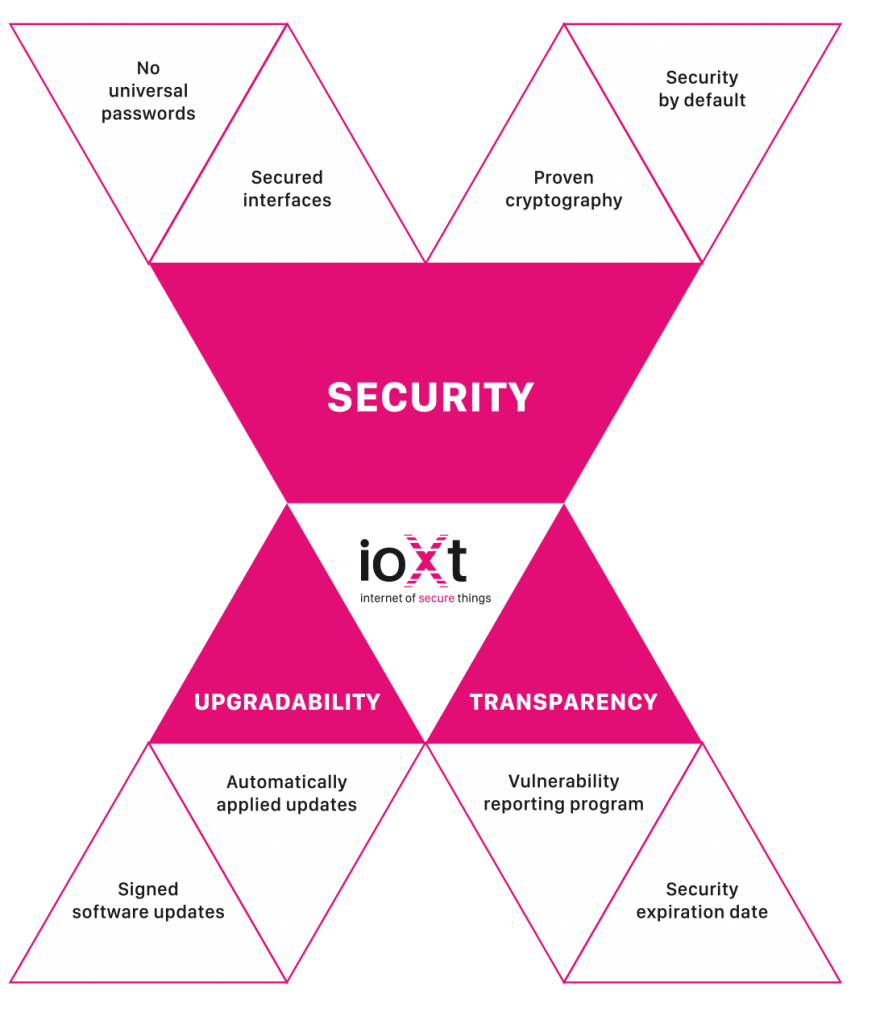
The Security Pledge is a promise that industry will work together to set security standards that bring three crucial principles – Security, Upgradability, and Transparency – to the market and directly into the hands of consumers, by ensuring the following specifications for secure IoT devices:
- No Universal Passwords: The product shall not have a universal password; unique security credentialswill be required for operation.
- Secured Interfaces: All product interfaces shall be appropriately secured by the manufacturer.
- Proven Cryptography: Product security shall use strong, proven, updatable cryptography using open, peer-reviewed methods and algorithms.
- Security by Default: Product security shall be appropriately enabled by default by the manufacturer.
- Signed Software Updates: The product shall only support signed software updates.
- Automatic Updates: The manufacturer shall act quickly to apply timely security updates.
- Vulnerability Reporting Program: The manufacturer shall implement a vulnerability reporting program, which will be addressed in a timely manner.
- Security Expiration Date: The manufacturer shall be transparent about the period of time that security updates will be provided.xiv
The companies that comprise the ioXt Alliance are committed to levying the tenets of the Pledge across the marketplace: Industry stakeholders will advance the tenets of the Pledge within their organizations and design processes, as well as within their respective trade and standards organizations. Retailers will demand and put on their shelves products that meet the Pledge’s tenets—as proven by pre-market validation—creating a supply and demand cycle that reinforces the Pledge’s principles and establishes the market’s heightened security expectations. And, in turn, developers will innovate to further advance security performance to help meet the commitments under the Pledge.
V. CONCLUSION: POLICYMAKERS SHOULD PROMOTE A NEW GLOBAL
INTERNET OF SECURE THINGS
The growing global IoT ecosystem offers tremendous promise for consumers and economies across the globe. It also, however, brings new security challenges that also must be addressed globally. Trying to confront IoT security challenges and threats—which do not respect jurisdictional borders—on a state-by-state, country[1]by-country, or even region-by-region basis will drive up costs of IoT devices without appreciably improving their security posture.
Fortunately, work on a better approach is underway. Industry, through the ioXt Alliance and other initiatives, has committed to advancing the security of IoT products. And industry’s commitments go beyond publishing recommendations and best practices: Companies in the ioXt Alliance are standing up real pre-market security certification processes that will meet current IoT security needs while also radically altering marketplace demands for IoT security.
Policymakers have a critical role to play in advancing this paradigm. The ioXt Alliance seeks to advance real and administrable obligations in IoT security—in a manner that accounts for and harnesses the global drivers of the IoT supply chain, and offers global solutions to the global challenge of IoT security. Rather than adopt jurisdiction-specific approaches that will fail to evolve as quickly as security threats do, policymakers should implement policy regimes that support and promote this game-changing global market-driven approach to security.










