Security often inhibits the sales process for embedded device OEMs. Customers don’t buy a product because it’s secure, they buy it because it does something they want it to do. From the customer’s point of view, as well as that of many salespeople, security is all downside risk that doesn’t contribute to the benefits of a product. However, with properly designed products, security can be changed from a sales inhibitor to an enabler.
Summary
- Security is the top obstacle to developing connected devices.
- In order to overcome security as a sales objection, secure product design is a prerequisite.
- Leading a sales discussion with security issues can pave the way for clear discussion of product features and benefits without lingering doubts about security.
The situation
Security issues inhibit IoT development and sales.
In surveys of electronics OEM engineers and executives, VDC Research has found that security is the No. 1 obstacle to development of connected devices, as exemplified by the findings in Exhibit 1.
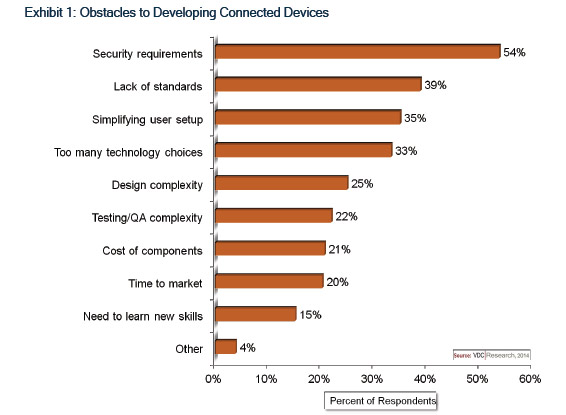
Similarly, in VDC’s in-depth interviews with OEM engineers and executives, many cite security concerns as a major reason why some of their customers are resisting device connectivity. The viewpoints of such customers are not unreasonable given the recent spate of high-profile data breaches. The damage done by a single security breach can far outweigh the potential cost savings and revenue enhancements achievable through the IoT. For IoT naysayers, security is a great excuse to say, “Nay.”
Furthermore, security represents a potential Catch-22 in the sales process between OEMs and their customers at precisely the time when a salesperson is trying to focus on the benefits of a product. Customers don’t buy a product because it’s secure, they buy it because it does something they want it to do. (An exception to this is a product like a router or firewall, where security itself is a core function of the device.)
From the customer’s point of view, as well as that of many salespeople, security is all downside risk that doesn’t contribute to the benefits of a product. (In a prior VDC View entitled, Connected, But Not Exposed, we described raising the issue of security as “akin to announcing that a big bad wolf is lurking in the forest.”) Raise the issue during a sales call and risk handing the customer a valid reason to hold off closing the deal; don’t raise the issue (or wait for the customer to raise it) and risk the customer thinking that the product must not address it adequately. This is particularly the case when selling to consumers, but it also applies to many enterprise and industrial customers, especially those that have not previously implemented IoT connected devices.
Collectively, these factors inhibit development and adoption of the IoT. Avoiding the Catch-22 requires a two-pronged approach: one in product design, and one in sales.
Vdc’s view
Design secure products.
This should seem obvious, but in order to sell security as a benefit, the product actually must be secure. Yet we regularly hear of product and system breaches that could have been prevented by designing and building products more securely, in some cases with relatively simple changes.

The use of hardware solutions, such as Trusted Platform Modules, combined with software techniques like code signing and application whitelisting, can make devices extremely secure. (It’s not a good idea to claim total impregnability, because attack vectors can arise unexpectedly, as evidenced by the Heartbleed bug in OpenSSL.) VDC has described many common methods for designing security into embedded devices in a prior VDC View entitled, Secure Hardening of Embedded Devices.
The appropriate level of security for a consumer entertainment product is different than for an aerospace product, but in either case, security needs to be considered early in the design phase so that it can be implemented into the hardware and/or software effectively and efficiently.
In addition, the design must factor in the ability to update security for the expected lifespan of the product in the field. This implies that firmware updating methods must themselves be securely designed, through the use digital certificates, hashes of the binaries, and the like. And the product plan must presume that a number of updates will be necessary (the quantity of which is dependent upon the type of product and its expected lifespan).
Assuming that the product is designed with adequate security, OEMs can then leverage security in the sales process.
Sell the security
This is where the approach we’re suggesting differs from the way most connected products are marketed and sold, and it is somewhat counter-intuitive: in order to overcome security as an inhibitor and turn it into an enabler, OEMs need to get security off the table as an objection at the outset of the sales process. Assuming that marketing efforts have generated sufficient interest in the category of product, selling can remove the downside risk of security by addressing it head on, before delving into product features and benefits.
In a corporate or industrial sales environment, particularly in face-to-face meetings, several techniques can help accomplish that:
- Clearly explain all the security technologies and features designed into the product. We can’t count how many times we’ve asked sales people about the security features of their embedded devices, only to receive vague responses such as, “Security? Sure, we have security,” yet they are unable to describe what the security features are. (The sales force must be adequately trained on the security features.)
- Don’t be afraid to pile on in-depth descriptions of security features. At this stage, customers will be concerned about whether the product has enough security, not whether it has too much.
- Address not only the product’s intrinsic security but also how it fits into the security of a connected system, including gateways, cloud services, etc.
- Make available technical experts who can answer security questions at a deep technical level. Consultations with technical experts don’t need to occur during the meeting (although that would be desirable), but the salesperson needs to convey that experts are readily available, and the experts really need to be available.
- Emphasize that in the event a significant security flaw is discovered, firmware patches can be distributed and installed in a secure manner.
- Provide case studies of customers who have successfully integrated the product into their systems in a secure manner.
For consumer products, it’s not necessary to cram the security features down buyers’ throats, but it is necessary to have detailed descriptions of security features that are easily accessible, such as through web links.
The primary objective of this sales approach is to remove security as an objection, so that the sales process can move on to discussion of the product’s main features and benefits. In this way, security changes from a factor that inhibits the sales process into one that enables it to proceed.
Salespeople may try to argue that they need to hook a customer on features and benefits before addressing security. But, until it is discussed, security is the elephant in the room.
Recommendations
Drive the impetus for secure development from the sales team.
Security is a major impediment to designing and selling connected products, but it would be pointless to try to leverage security in the sales process if security isn’t built into the products. Therefore, the sales staff should be at the forefront of requesting security features from the engineering organsation.
Test security independently.
Products not only should be tested for security by an in-house QA department; security should be tested by an independent firm that specialises in penetration testing. Unless security is tested by experts, you don’t know what you don’t know about potential security flaws in your products. Better that you discover security flaws before your customers do.
Lead with security in the sales process.
Get the elephant out of the room first, so that customers can focus their attention on the product’s functional features and benefits. VDC’s market research indicates that customers are already wary of security issues for connected products, and unless security issues are overcome first, security concerns may taint customers’ perceptions of features and benefits. Addressing security up front also helps convey confidence that a manufacturer is paying attention to security issues and takes them seriously.










