Cynet announced the future of extended detection and response with the launch of Cynet 360 V4.0. The new generation autonomous breach prevention platform now features XDR, 24/7 Managed Detection & Response (MDR) and full Response Automation, improving cyber threat detection accuracy while reducing the complexity and overhead required for comprehensive defense and mitigation of sophisticated and subversive cyber-attacks.
Cybersecurity professionals now deploy multiple prevention and detection technologies to defend an endless variety of vulnerabilities and attacks to endpoints, networks, users and data. While these tools generally do a fine job preventing and detecting the vast majority of cyber-attacks, Cynet says they continue to miss the edge cases – the difficult to identify attacks that slip through the cracks between these point solutions. Visibility across the environment and understanding the context of security data and alerts is required to solve this complex problem.
According to Gartner, “Extended detection and response (XDR) solutions are emerging that automatically collect and correlate data from multiple security products to improve threat detection and provide an incident response capability. For example, an attack that caused alerts on email, endpoint and network can be combined into a single incident. The primary goals of an XDR solution are to increase detection accuracy and improve security operations efficiency and productivity.”
Cynet 360 V4.0 aims to set new standards in the cybersecurity space. Advanced capabilities include:
- Full threat visibility: Cynet 360 V4.0 provides complete visibility across the entire environment. The detection power achieved by natively combining signals and data from multiple sources simply cannot be matched by siloed, point protection solutions. Even the most subversive attacks are fully exposed with pinpoint accuracy by Cynet.
- Complete cyber threat prevention and detection: Cynet 360 V4.0 provides multiple, integrated prevention technologies to block standard and advanced attacks across the environment. Deception technology is also built-in to entice cybercriminals that have penetrated the network into exposing themselves before they do real damage.
- Incident orientation: Centralising the signals from multiple detection sources allows Cynet 360 V4.0 to group related alerts and data into incidents. Incidents include all related alerts and indicators of compromise (IOCs) related to an attack and fully automates root cause analysis, threat impact determination and remediation actions.
- Response automation: Cynet 360 V4.0 provides fully automated response tools for cross-environment investigation and remediation. Investigations are fully automated – first determining the root cause and then analysing the full breadth and impact of the threat.
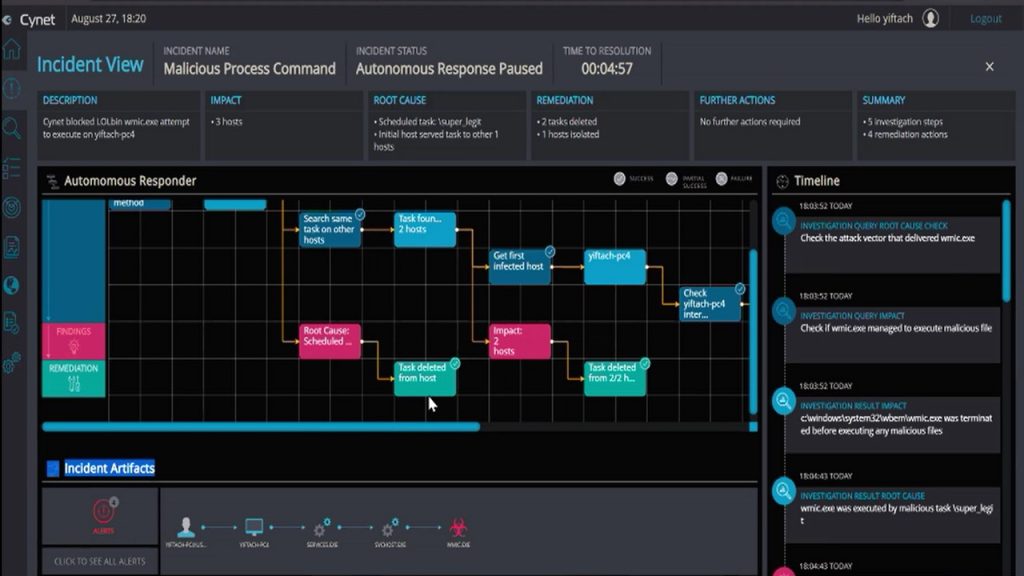
New to Cynet 360 is the unique and insightful Incident Engine(1), an automated response capability that produces a visual map of an entire incident investigation and response. In as little as five minutes, the advanced tool automatically performs a full incident response workflow, including root cause analysis, full threat impact determination and all necessary remediation actions – significantly reducing the mean total time to contain and eliminate real threats.
Complementing the Cynet 360 V4.0 offering is the addition of the CyOps 24×7 detection and response services team. CyOps is a team of world-class cybersecurity experts that continuously monitors all Cynet customer environments 24/7 to ensure any attacks are uncovered, provides ad-hoc threat investigations and forensic analysis, and guides users through any necessary remediation steps.
“Because cybercriminals find ways to circumvent the cocktail of security solutions in place by most organisations, we are answering the call to strengthen and simplify the process,” said Eyal Gruner, CEO and co-founder of Cynet. “Cynet 360 V4.0 provides the security operations centre (SOC) with a complete view of cyber threats to applications, endpoints, system networks and overall IT infrastructure where automated processes are executed to detect, analyse, hunt, and thoroughly resolve threats.”
Comment on this article below or via Twitter: @IoTNow_OR @jcIoTnow










