In some ways, the Internet of Things is aptly named, especially when it comes to security. There are a lot of things to worry about.
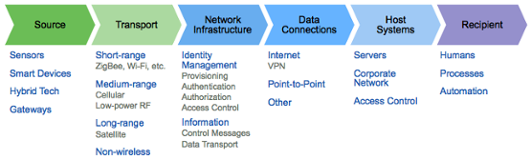
IoT risk management point categories include the source, transport, network infrastructure, data connections, host systems, and recipients. Within each point are hundreds, possibly thousands, of components—each of which offers hackers a potential opening to infiltrate the infrastructure.
A 360-degree approach
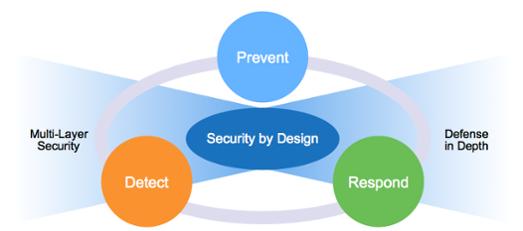
Implementing IoT security can seem overwhelming; so much so that many companies simply assume their service providers have it covered. That puts tremendous pressure on your operations, especially if a breach occurs. The secret to successful IoT security is to take a 360-degree approach to your operations, following three basic tenets—prevention, detection, and response, says Carmi Brandis of Aeris.
Prevention: Involves network ‘whitelisting’ and traffic segregation. Whitelisting is accomplished by controlling both device and systems access. Traffic segregation prevents unauthorised mobile-to-mobile communications from taking place, a vital security measure in our increasingly untethered world. The recent Jeep incident, caused by a weakness in peer-to-peer communications, could have been prevented had the vehicle infrastructure incorporated security levels of device access based on traffic segregation.
Detection: With IoT is a lot more complicated than with the cloud or web solutions. For example, a hacker can turn a device into a ‘sleeper cell’ right at the manufacturing level, before it ever goes online. IoT detection includes both anomaly and timely elements. Anomaly detection recognises compromised devices through data transmission patterns.
Even a sleeper cell would be immediately exposed once activated. Timely detection requires early and/or instantaneous (as with the sleeper cell) detection. Many hacks can remain hidden for years, as evidenced by the LinkedIn and Yahoo breaches. In Yahoo’s case, the undetected attack dramatically lowered the company’s sales price.
Response: Is a two-prong approach, immediate and measured. If a breach occurs, the system blocks the affected devices on the fly, thus minimising the impact on other applications. Measured response makes your devices proactive by requiring verification for all over-the-air updates. Only authorised updates are allowed for security fixes.
No IoT system will ever be foolproof, unfortunately, but by approaching security from a comprehensive ‘every view’ standpoint, you greatly increase your chances of winning every battle.
Contact us to find out how Aeris can heighten the security for your deployment.
The author of this blog is Carmi Brandis of Aeris
Comment on this article below or via Twitter: @IoTNow OR @jcIoTnow










