As well as reducing the cost and complexity of deploying IoT, embedded SIM can become the root of trust to deliver critical IoT applications relying on rich edge-to-cloud deployments, writes Matt Hatton, the founding partner of Transforma Insights.
Transforma Insights forecasts that by 2030 there will be 27.8 billion connected IoT devices, of which almost five billion will be connected using cellular technologies. Such market forecasts represent our best estimate of how the market will evolve. However, in such a fast-moving space, with rapidly changing technologies and business models, there are many potential developments that could accelerate, slow or alter the nature of the market evolution. Two contrasting developments define the state of IoT today: richer functionality and constrained environments. The balance between them will define the extent to which the market might exceed, or fall short of, those forecasts.
Source: Transforma Insights, 2021
IoT’s richer functionality and greater constraints
Firstly, we see increasingly rich functionality and capability aimed at deriving huge amounts of value from connected devices. Cloud and edge computing, machine learning, mobile private networks and 5G are just a few examples of richer functionality being applied to IoT. Furthermore, it is becoming increasingly evident that enterprises are using IoT for more critical systems, with the consequent requirement for more sophisticated features and capabilities, not to mention more robust security.
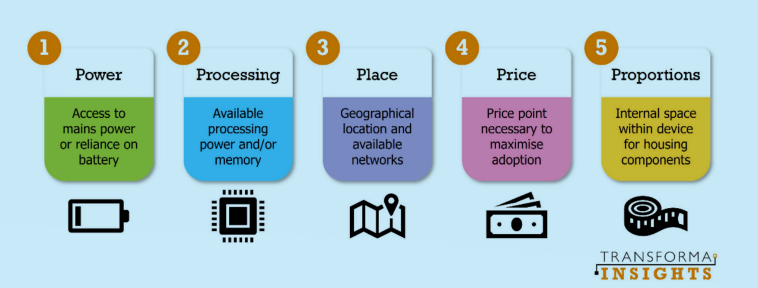
At the same time, an almost contradictory trend is occurring. IoT technologies are being rapidly refined to support applications deployed in highly constrained environments. Large volumes of connections must cope with limitations on, for instance, access to power, physical and cost limitations on componentry, and geographical remoteness limiting availability of networks. We refer to these constraints as the five Ps: power, processing, place, price and proportions.
The key to overcoming these constraints is in delivering what we at Transforma Insights term Thin IoT. This consists of, across each of five layers (device hardware, device software, networking, middleware, and edge computing and machine learning) an optimum set of technologies for supporting IoT in constrained environments. These include system-on-chip, chip-on-board, embedded operating systems such as TinyOS and RIOT, networking technologies such as message queuing telemetry transport (MQTT), constrained application protocol (CoAP), and low power wide area (LPWA) technologies, thin middleware, and data processing techniques such as tiny machine learning (TinyML).
Putting these two trends together places a strong requirement on the market to deliver cost– and energy-efficient solutions which are also capable of taking advantage of all the latest new technologies in order to deliver the optimum capabilities for the enterprise. One key technology which can greatly support both of these sets of demands, particularly as applied to cellular-based IoT, is embedded SIM (eSIM), all wrapped up with inherent trust.
eSIM/iSIM as a trusted enabler for IoT growth
The physical machine form factor (MFF2) embedded SIM has been available since 2016 and the ability for remote SIM provisioning (RSP) for several years before that, finally being standardised in 2016. Since then, the integrated SIM (iSIM) arrived in 2018 moving the SIM functionality to a secure location on silicon along with the application processor and radio, all implemented on the same system-on-a-chip hardware.
The new form factors mean cheaper, smaller and lower-powered devices, helping to address many of the constraints on IoT. Use of MFF2 chips is cheaper than the removable alternative, meaning the bill of materials will be directly reduced. Using iSIM will even further reduce the cost. Similarly, with a smaller footprint they also allow for smaller, lighter, devices with lower manufacturing and shipping costs – as well as probably a more appealing form factor, which might be important for some use cases. There are supply chain savings associated with being able to put the IoT device into field without needing to switch out the physical SIM card. The eSIM/iSIM will also have a longer lifespan, both because of being more robust – particularly in harsh environments of extreme temperatures and/or vibration – and also due to never needing to be swapped out. We should note, of course, that there is a cost associated with subscription management, but this is very modest in comparison to the cost savings that can be made.
The MFF2 devices, and iSIM even more so, also require lower power, for instance being able to awaken from power saving mode (PSM) to enact eSIM provisioning. For IoT solutions working in highly constrained environments, this can provide a significant benefit. It should be noted, however, that applications that are highly price– and power-sensitive may opt for narrowband IoT (NB-IoT) as the enabling technology, attracted by lower module costs, longer battery life and – probably – lower data charges. However, this can be incompatible with using remote SIM provisioning since it often relies on SMS, which isn’t supported in lots of NB-IoT networks and devices. Mobile network operators (MNOs) should prioritise resolving this issue through the device management platform.
Embedded SIM is not just about cost and power savings, of course. It is also critical for enabling the richer set of IoT capabilities and the deeper integration of IoT into enterprise processes. As enterprises increasingly entrust their business-critical systems to IoT, two issues at which eSIM excels become increasingly important: security and device-to-cloud integration.
Cloud and edge computing are increasingly common features of IoT deployments. The migration of applications to the cloud has been happening for the last decade and will continue for the next. This has driven increasing interest from cloud hyperscalers, particularly AWS and Microsoft, in IoT. The moving of application logic to edge devices and the network edge to reduce latency and give more autonomy had created an increasingly complex environment where application logic, data and processing sit in multiple places, be it in the cloud data centre, the network edge, the gateway or the edge device itself. This complexity necessitates much greater consideration of how transport is secured end-to-end, from device to cloud server. Through the recent IoT SAFE initiative, the SIM can help to provide increased end-to-end security when connecting IoT devices to cloud services.
A further benefit of eSIM is its ability to future-proof technology choices in radio access networks. Today there is a patchwork of different technologies available, with NB-IoT, LTE-M and 5G being rolled out and 2G and 3G networks being gradually switched off. Remote subscription management significantly reduces the exposure to network sunsetting, by allowing connections to be switched across to alternative available networks.
What is IoT SAFE?
The IoT SIM Applet For secure End-to-end communication (IoT SAFE) is a mechanism for ensuring end-to-end security for IoT data flows, from chip to cloud. It establishes the SIM card as a hardware Root of Trust, a source that can always be trusted, storing private keys and certificates in a secure element (SE) that can be used to authenticate the end device and provide credentials for the IoT application. The SIM is the optimum place for this hardware root of trust. It is fully standardised, interoperable and highly secure. The SIM establishes a datagram transport layer security (DTLS) session with the other end point – typically a cloud server.
Transport layer security (TLS) refers to end-to-end security for data communication between endpoints. A subset of that, which applies particularly to IoT, is DTLS, which specifies requirements related to data sent in a connectionless way so the sending device need not wait for the receiving device to be ready, will not seek confirmation that the packets have been received, and data packets need not be guaranteed delivery in a particular sequence or at a particular time. Most IoT applications rely on datagram-based technologies such as user datagram protocol (UDP). As a result of being connectionless, UDP is a lighter protocol requiring much less network resources and less processing on the device. Therefore, it is much better for constrained IoT devices.
Essentially, IoT SAFE is about applying to end-to-end transport of data a similarly high level of security that SIM brought to network access. Rather than just authenticating the SIM onto the network, this authenticates the IoT application into the cloud.
The arrival of eSIM and iSIM provides a valuable tool for addressing the challenges of the constraints under which IoT must work, at the same time as providing tools to better secure the much-needed device-to-cloud data stream.
Become guardians of trust in IoT
MNOs haven’t been very active in embracing eSIM. Partly this is because of the relative immaturity of the systems, particularly anything more than simple initial bootstrapping and localisation of a device. Most of their reticence, though, stems from the complexity of implementing the system. It’s quite straightforward to deploy the eSIM technology via the embedded universal integrated circuit card (eUICC), subscription-manager data preparation (SM-DP) and subscription manager secure routing (SM-SR), although integrating with other MNO SM-SRs is a minor logistical hurdle. What is less simple is to manage the impact that eSIM has on other commercial and operational elements such as billing, customer care, inventory, device lifecycle management, legal, network planning and numerous other systems. The other reason for reticence is competitive: there is a persisting concern that allowing the switching of devices off the network is a competitive threat. Despite the MNOs’ reservations, there is no escaping the fact that the future of cellular IoT is eSIM, and eventually iSIM. The cost and energy savings associated with using the technologies, as well as the increased redundancy provided by being able to switch operators, will mean that IoT adopters will demand eSIM/iSIM and MNOs and Mobile Virtual Network Operators (MVNOs) will need to meet that demand. As cloud providers accelerate the expansion of their IoT capabilities, they will also demand the end-to-end security which is supported by IoT SAFE. There are also further benefits to MNOs in pushing the cost of SIM cards onto the hardware value chain.
MNOs have the opportunity to place a secure hardware element that they control into the device from day one and establish that as a root-of-trust for many aspects of the IoT application. This will deliver an additional layer of capability within cellular communications. It will also, through the standardised and interoperable transport layer security, provide the MNO with an additional critical role in supporting the deployment of high value secure IoT. If MNOs were reticent about eSIM, the ability to establish themselves as the guardians of trust in the IoT should make them think again.
What is critical for MNOs is to move relatively fast and in collaboration with fellow operators. Historically, there are many examples of technologies where the operators should have been able to establish a strong position only for delayed and over-complicated solutions such as mobile payments or unified communications to be supplanted by more nimble alternatives such as Apple Pay or Slack. The track record of the mobile industry in inserting itself into vital growth areas is not particularly good. With eSIM and the hardware root-of-trust there is the opportunity to do so, particular where the MNO can exert influence over the hardware value chain to embed the functionality as early in the manufacturing process as possible.
Balance functionality with simplification
The key to accelerating the adoption of IoT is in balancing functionality with simplification. IoT solutions have always involved a lot of (sometimes literally) moving parts. Few technology disciplines have to deal with such a diverse range of technology fields, spanning hardware, software and connectivity. Over the last decade or so many developments have helped to simplify the process of deploying IoT; the platformisation of the software space being one good example. In other areas, things have become more complex, not least in the provision of wide area connectivity where a single dominant technology – general packet radio system (GPRS) – has given way to many including: GPRS, LTE, NB-IoT, LTE-M, 5G, LoRa, Sigfox and others. Beyond that, the arrival of edge computing and machine learning adds a further layer of complexity. Delivering IoT is a constant battle against complexity while at the same time harnessing the amazing technology tools that are available.
Initially, eSIM and iSIM may seem like further complications in how IoT is delivered. The reality is, however, that for adopters they represent a significant simplification, future-proofing vendor selection and streamlining supply chains. The use of the SIM as a root-of-trust also simplifies the inevitable requirement to integrate IoT data into cloud environments. Having that root-of-trust capability embedded in the device from day one removes one more complexity burden. The other big advantage with IoT SAFE is in the zero-touch provisioning to cloud services, again simplifying the process of integrating IoT.
MNOs can, with the benefit of eSIM, enhance the functionality delivered to customers of cellular IoT solutions, while at the same time simplifying adoption.
Comment on this article below or via Twitter: @IoTNow_










