The IoT market is set for continued robust growth up to 2030, writes Robin Duke-Woolley, the chief executive of Beecham Research. According to Statista, almost 30 billion IoT devices are expected to be connected by 2030, up from nearly ten billion in 2020 – a CAGR of nearly 12% over the decade. This includes both long range and short range devices. According to Ericsson’s mobility report of June 2023, cellular represents around 20% of this, growing slightly faster at over 12% per annum.
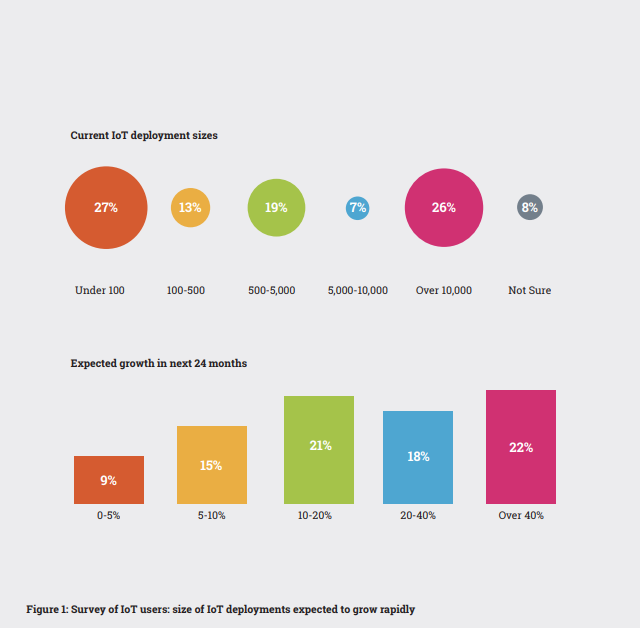
Not only that – the size of individual IoT deployments is growing much faster. Recent research indicates the growing expectation among IoT users of individual deployments growing rapidly over the next few years. An example of this is a recent survey of IoT users by Beecham Research, some of the findings of which are illustrated in Figure 1.
As Figure 1 shows, more than a quarter (26%) of respondents already had deployments of over 10,000 connected devices, and a majority (52%) with deployments of more than 500 connected devices. In addition, there is an expectation of high growth of existing deployments in the near future, with as many as 22% of respondents expecting over 40% growth in the next 24 months. This is not an unusual finding – it confirms that substantial growth of individual deployments already in the field is under way.
Within that, the largest proportion of these IoT connections are expected to be low-cost devices that are small in size, have limited processing power and storage, are battery driven and may be expected to run for ten or more years. These resource-constrained devices must remain connected to deliver sensor data and act upon commands from remote locations, and they must do this securely. Secure identities are required to identify these devices and their data, as well as protect them from misuse by remote attacks. The sort of use cases this covers are sensors, trackers, wearables – including health related – and other low-cost devices that will increasingly form the backbone of IoT. These form a myriad of data sources providing up to date information on our world and how we live.
The growth rate of these devices is expected to be faster than the overall IoT market growth figures, primarily because of the rapidly growing need for connected data sources to support commercial operations.
This raises some vital questions, such as:
- How will these all be connected?
- How will they be powered?
- How will they be managed and updated?
- How do you ensure the data from them is sufficiently secure to trust it?
- Most of all, how do you make this easy for users to implement in the very large numbers envisaged anywhere in the world?
Taking this last point, for such large numbers of devices, connecting them securely must be a completely smooth operation where the user does not need to understand the technology – just switch on and go.
There is a growing consensus that standards-based embedded SIM (eSIM) technology and its integrated form factor (iSIM) provide a particularly appropriate basis for responding to these questions.
From removable SIM to standards-based eSIM and iSIM
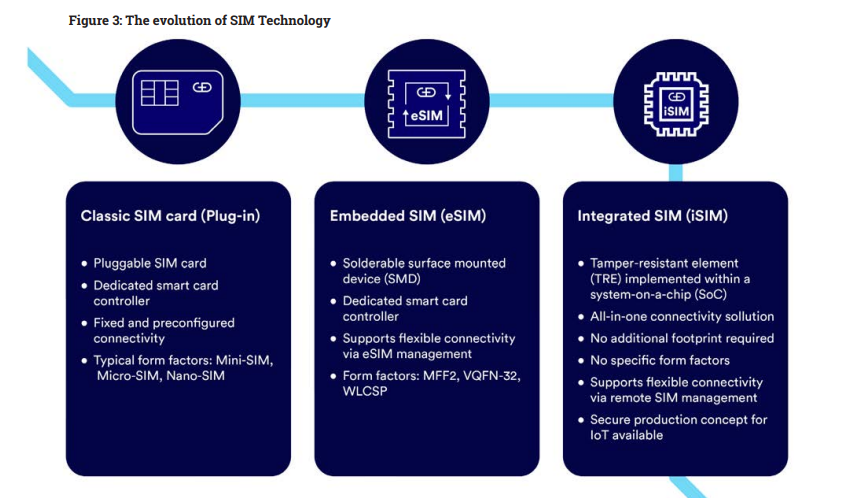
The physical SIM card has been part of cellular connectivity since 1991, when it was first brought to the market by Munich smart-card maker Giesecke+Devrient (G+D), who sold the first 300 SIM cards to the Finnish wireless network operator Radiolinja. It plays a leading role in many consumer mobile devices and IoT deployments and there have been several developments to reduce the size – from mini, to micro and nano. However, the SIM market is evolving rapidly, and newer options eliminate the need for a removable SIM.
First brought to market in 2012, the eSIM is soldered to a device’s printed circuit board and introduced a way to send SIM profiles to devices over the air (OTA) using remote SIM provisioning (RSP).
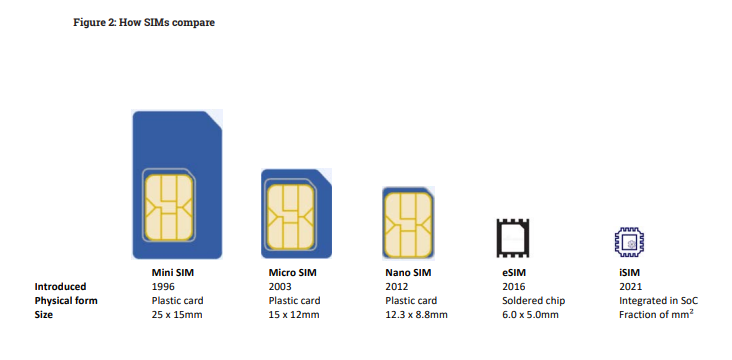
The newest iteration is the integrated SIM, first brought to the market in 2021. This streamlines the eSIM’s functionality by porting it into a system-on-a-chip (SoC) architecture, which means the SIM does not require dedicated hardware while also enabling remote SIM provisioning over the air.
The classic or removable SIM is a removable card that comes in various sizes. First developed for the consumer mobile phone market and inherited by the M2M industry, it has evolved into new form factors to fit smaller devices. They are straightforward and convenient for consumer applications and some IoT use cases. However, they present significant logistical and reliability issues for large-scale IoT device deployments as well as physical security concerns including theft.
For example, installing removable SIMs in manufactured products such as in the automotive sector used to be logistically difficult and expensive. They could not be installed in the factory – they had to be installed where each car was sold and used, to ensure each one was connected to the right mobile network. That introduced often substantial logistical issues to ensure that the right SIM reached the right car in the right country at the right time. The switch to eSIM helped to resolve these issues and, as a result, has led to a considerable expansion of the connected car market.
In addition to this, when an organisation switches mobile network and needs to change device profiles, removable SIMs are convenient in some use cases — users can simply remove the old SIM and plug in the new one. However, removing and replacing SIM cards on thousands of devices in large-scale IoT deployments can be costly or even impossible. If these devices are themselves low cost, then the physical replacement of individual SIMs may be considerably more costly than the devices themselves.
Although removable SIMs are easy to access, they are also subject to theft or tampering. Such SIMs must be continuously monitored to ensure they have not been removed and placed in other devices.
The eSIM was developed in response to the shortcomings of removable SIM cards for IoT. In particular, the connected car industry pushed eSIM forward. Automotive OEMs were motivated to create a tamper-proof SIM with more robust security that could be remotely provisioned with the right network profile. Such a SIM would serve their connectivity needs and protect against extreme environmental conditions, including dust, moisture, temperature and vibration.
Today, the automotive industry has adopted the technology widely, and all connected cars use a soldered eSIM as a single stock keeping unit (SKU). The embedded universal integrated circuit card (eUICC) standard makes the eSIM versatile. It allows remote provisioning of the hardware with network profiles. The standard allows mobile network operators (MNOs) to send their SIM profiles to eSIM devices remotely. By eliminating the need for physical access, the eUICC enhances connectivity management for secure IoT deployments at scale.
The eUICC standard also enables multiple profiles to be loaded. Devices can be manufactured for use in multiple geographies. Then they can be switched to the appropriate regional connectivity provider profile when the device is deployed or moved.
The iSIM has been developed to cater for cost-optimised devices that are efficient in terms of data and energy consumption and bill of material (BOM) costs. These use cellular IoT low power wide area network (LPWAN) options, such as NB-IoT and LTE-M, to address this IoT market need. iSIM technology incorporates the SIM operating system (SIM OS) into the cellular module hardware.
Unlike removable SIM cards, which are set into plastic housings, or eSIMs, which are soldered into the device, an iSIM (or iUICC – integrated UICC) is a tamper-resistant element (TRE) within a system-on-a-chip (SoC). It is an isolated hardware component combined with a baseband chipset to create a single connectivity module. The iSIM also saves space in hardware design. Every square millimetre makes a difference for size-constrained applications – particularly wearables. Since it does not require physical space for an eSIM chip or removable SIM card, the iSIM can also substantially reduce the device footprint.
With iSIM functionality built into the base cellular module hardware, the result is savings from eliminating components including SIM trays, SIM cards and eSIM chips. As a result, it is physically over 90% smaller than an eSIM chip. At the same time, it is particularly power efficient as the SoC itself powers the iSIM, which only uses power when it is actually being used for authentication. In addition, because the iSIM resides within the SoC and is directly connected to the SoC bus rather than through an interface to that bus, the performance is increased.
Security is also enhanced through the operation of the hardware TRE itself. The combination of hardware and software elements is very important. A secure software element on its own can always be hacked. If that structure can be changed, it can be cloned, impersonated or interfered with in many different ways. Secure hardware, on the other hand, is much more difficult. This is because hardware security involves burning secure identifiers/ credentials into the hardware, which cannot then be physically tampered with or extracted. This is called a secure Root of Trust and considerably more secure than anything else. As such, it provides a secure basis on which to build a variety of value-added services that require very high security – see section on IoT SAFE later.
What’s special about iSIM
In this way, and in order specifically to cater for low cost, low power, constrained IoT devices, the iSIM has been designed to be the most cost-efficient SIM connectivity solution over the device lifetime.
The iSIM is now standardised along with the eSIM and together they have been catered for in three main Remote SIM Provisioning specifications – see section on RSP specifications for devices later. Key points to note from this:
- The iSIM, the integration of the SIM into the baseband chipset, has paved the way for the next generation of secure IoT connectivity – in constrained devices
- The iSIM continues the success of SIM and eSIM in authenticating mobile networks without reducing security
- The iSIM ensures secure data processing while providing interoperability within the eSIM ecosystem
- For the foreseeable future, SIM, eSIM, and iSIM will coexist because they provide similar but also differing characteristics targeting varying areas of the IoT market
- The iSIM can be easily integrated into IoT solutions and enables secure device management during the entire lifecycle
- Since 2021 the iSIM is commercially available and has been proven in the field
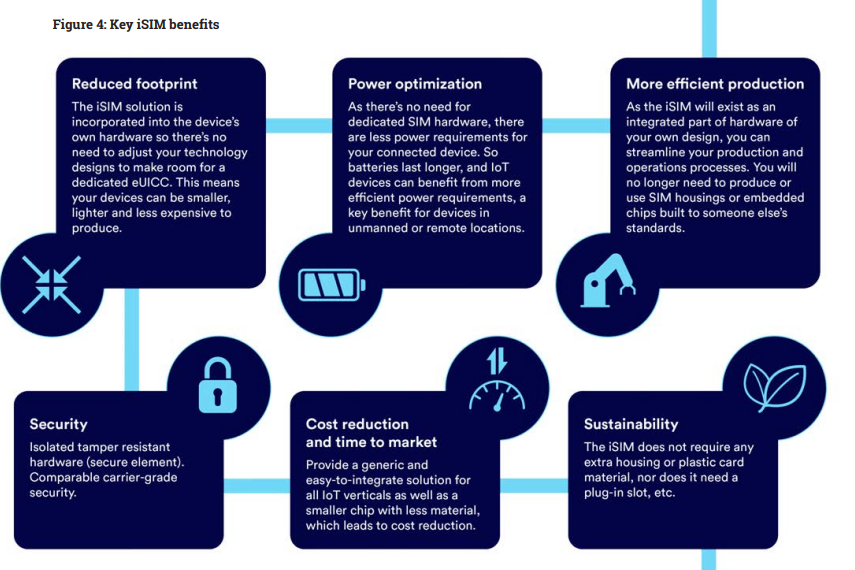
The iSIM has several features that help make it a more robust, secure phase of SIM card technology. These features have been designed by industry experts to meet agreed-upon, approved specifications, standards, and processes. As the latest phase of the SIM evolution, the iSIM offers several advantages and opportunities:
- Reduced footprint: embedded into the device’s hardware, it allows for smaller, lighter devices that are less expensive to produce
- Power optimisation: lower power requirements means that batteries will last longer and IoT devices will benefit from greater efficiency
- More efficient production: integrating the iSIM as part of the baseband module can streamline production and operation processes
- Security: The isolated, tamper-resistant hardware element (TRE) is highly secure both physically and electronically
- Reduced cost and time to market: a generic and easy-to-integrate solution for all IoT verticals, as well as a significantly smaller chip that saves space, time and materials
- Sustainability: no extra housing or plastic, reduced power consumption and a much smaller size makes this the greenest SIM solution
RSP specifications for cellular devices
As noted earlier, there are three main RSP specifications for cellular devices. These are:
- M2M (SGP.01/02)
- Consumer (SGP.21/22)
- Constrained IoT (SGP.31/32)
There are two standardised eSIM remote provisioning specifications currently in use designed by the GSMA: the Machine-to-Machine (M2M) eSIM Spec and the Consumer eSIM Spec. The M2M Spec is designed for IoT devices such as sensors that may operate without a user and have no user interface – so-called headless devices. It is implemented via SGP.02. However, this standard is based on SMS text message communication and is therefore neither efficient nor future-proof, since MNOs are now switching off SMS-based messaging.
In contrast, the Consumer Spec is designed for user devices such as smartphones and tablets, where there is a user interface. This makes managing profiles simple, only requiring user consent to add a new profile or switch between profiles. It is implemented via SGP.22 that relies instead on IP-based communication.
As a result of this, a new RSP SGP.32 standard for constrained IoT devices has been designed. This is similar to the successful SGP.22 for consumer devices but specifically caters for IoT devices with no interface – headless devices. As a result, iSIM with RSP functionality follows this standard.
Standardisation of the RSP specifications belonging to the SGP.32 family have now been finalised but it will take until 2024 for iSIM products with full RSP support to reach the market.
RSP and SIM profiles
In addition to the SIM OS, one or more SIM profiles are usually loaded onto an RSP-enabled SIM (mainly eSIM or iSIM, but in some cases a removable SIM) so that it can use them to authenticate itself to the respective network operator. Managing profiles goes within a few seconds when using a broadband connection. In the case of narrowband IoT, this can take longer. The administration is done in the background via an end-to-end secured connection to the RSP server.
As noted earlier, one of the great advantages of RSP is the single SKU. All devices can be produced identically, which significantly simplifies logistics as well as the production process and leads to cost savings. The decision as to which profile is to be used or loaded is only made when the device is commissioned for the first time. In practice, there are different use cases for which the use of the RSP technology is beneficial:
a) Switching between previously loaded profiles to adapt the IoT device to the best connectivity at the device’s location (national or international), for example. This can also be used to keep roaming costs as low as possible. The SIM memory typically limits the number of pre-loaded profiles. If the change does not work, the device is switched to the original profile or to an alternatively available profile.
b) During the lifetime of an IoT device, it may be necessary to exchange a previously loaded profile. This may make sense for cost reasons, for example, or because the device is to be operated in a country not previously considered, or because a network operator has discontinued its service. In these cases, before changing a profile, assuming there is enough free memory on the SIM, the new profile must be loaded via the mobile network. Profiles that have already been loaded but are not active can also be deleted via RSP to free up memory. After the new profile has been successfully loaded, the change can be completed. Here, too, the system switches back if the activation of the new profile is not successful.
c) While previously loaded profiles with an international mobile subscriber identity (IMSI) incur costs even when not in use, using a so-called bootstrap profile offers a cost-effective alternative. Bootstrap profiles are designed by default to allow download of a permanent profile. They enable devices to connect to any available mobile network – whenever a device is turned on for the first time and wherever they are operated in the world. This enables a device to ‘auto-configure’ itself the first time it is switched on in the destination market.
G+D’s technology maximises efficiency by using this bootstrap profile in order to enable massive deployment of devices at low cost and allow downloads of additional operational profiles as needed. Permanently connecting to a bootstrap profile to transfer device data is not possible – it connects only to the RSP server, but not to any other network operator. During the lifetime of the IoT device, it is also possible to switch back to the bootstrap profile to load another profile in the event of a fault or for other reasons.
IoT SAFE
The eSIM and iSIM have introduced tamper resistant elements (TRE) that enhance the security aspects of the SIM to a higher level, both physically and electronically.
The standardised eSIM specification was developed by the GSMA as a response to the problems of using the traditional removable SIM cards in IoT devices. A further GSMA initiative is the IoT SIM Applet for Secure End-to-End Communication (IoT SAFE). This recommends that the industry should use the SIM as a hardware TRE or root of trust to achieve end-to-end, chip-to-cloud security for IoT products and services. It is widely accepted technically that the SIM is particularly well-suited for this purpose: it is one of the hardest of all identifiers to spoof, with advanced security and cryptographic features, is fully standardised, and has been deployed in huge numbers of devices for the past 30 years. Key characteristics of IoT SAFE include:
- Use of the SIM/eSIM as a mini ‘crypto-safe’ inside the device to securely establish a TLS session with a corresponding application cloud/server
- Compatible with all SIM form factors such as eSIM and iSIM. eSIM/iSIM are particularly suitable for IoT SAFE since they are certified
- Provides a common application programme interface (API) for the highly secure SIM to be used as a hardware root of trust by IoT devices
- Helps solve the challenge of provisioning millions of IoT devices
The IoT SAFE applet runs on Java virtual machine, which in turn runs on the SIM OS.
Choosing the right SIM for your deployment
When selecting a SIM type and form factor for your IoT deployment, start by considering cost structure because it reflects the business model behind the device. For example, in the automotive sector, the cost of the final product might motivate you to invest in expensive chips. Embracing a less expensive platform would mean compromising on resiliency and security.
If your product is a low-tier device such as a pet tracker, spending an extra dollar or two on hardware per device could eliminate your profit margin. In that case, seeking a low-cost iSIM solution makes sense.
Also, consider whether the use case will require remote provisioning. While eSIMs are best known for this feature, all form factors are candidates for eUICC software that enables OTA profile updates. GSMA has designed a large-scale provisioning scheme for the IoT space, allowing MNOs to provision devices in large volumes simultaneously.
The future of SIM technology
In spite of the huge growth of eSIM and iSIM, traditional SIM cards continue to exist in the IoT market — at least for now. In many countries, prepaid service remains the predominant way to connect, making traditional SIM cards the most practical choice.
For high-end IoT use cases with an inherently higher cost structure that require a high degree of MNO acceptance from the first day, eSIMs are an ideal solution. iSIMs will come into play for low-tier IoT connections where device size and energy efficiency are necessary strengths. There is a lot to consider when choosing between SIM, eSIM and iSIM. Depending on the use case, there is room for every form factor and SIM type for the foreseeable future.
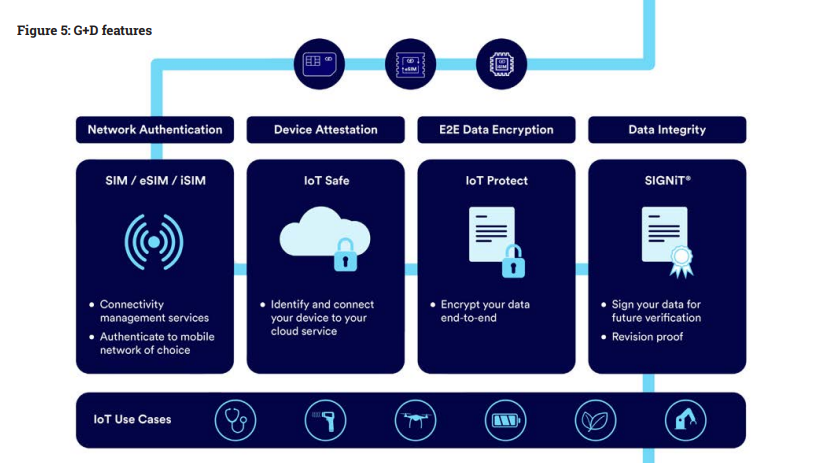
How G+D helps
The G+D IoT Security Suite protects data generated from IoT devices. The suite supports cellular and non-cellular devices. Its core services are IoT Safe, IoT Protect and SIGNiT. The platform covers both the backend and SIM software. It enables mobile operators to offer a consolidated toolbox to OEMs and enterprises. They, in turn, are able to manage SIMs and other devices over the entire lifecycle – from manufacturing and activation, to managing subscriptions and policies, all the way to deactivation.
- IoT Safe
Companies build IoT solutions for the marketplace, and these devices connect to cloud platforms. The credentials, however, are mostly stored within the application processor memory. This makes them an easy target for attacks. The G+D IoT Safe protects against threats and provides cybersecurity by adding a secure element (a SIM card) to the IoT device. It is equipped with an applet that assists with the authentication to the cloud provider. In addition, this offering includes a credential manager that controls and replaces factory credentials. We also offer a device toolkit that provides documentation, which includes the sample code that is used to assist the IoT device developer in securing the communication between the IoT device app and the SIM applet. - IoT Protect
The overall functionality of IoT Protect is to provide an end-to-end encryption/decryption mechanism for IoT applications. Information is transmitted securely between the IoT device and the backend, independent of the communication channel (broadband, NB-IoT, Wi-Fi, etc.). Common applications for IoT Protect are those in which data transfer is low, which is typical for low-end and battery-powered IoT devices. - SIGNiT
SIGNiT is the solution that provides data integrity for multi-party IoT ecosystems. It helps sign every packet of IoT data generated so that they can be verified in the future – starting directly at the source: the IoT sensor. Digital signatures for its data are provided by either the SIM or eSIM.SIGNiT combines secure and proven SIM environments with blockchain technology. It allows enterprises to easily digitalise and secure processes in a decentralised ecosystem while providing IoT users with comprehensive and robust security for data generated by IoT devices. The solution has already been successfully implemented in commercial environments, and has potential in sectors like logistics, agriculture, energy and the automotive industry.
A recent example: SIGNiT enables Lufthansa Industry Solutions to ensure that IoT data is 100% trustworthy – featuring G+D’s awarded security technology and an innovative blockchain by Cologne-based start-up Ubirch. Ubirch has developed a trust protocol, which ensures that data from IoT sensors cannot be falsified after they are generated. The data packets of these sensors are sealed with strong cryptography in a way that it becomes technically impossible to manipulate them once stored in a blockchain. This combination of offering blockchain on a SIM is unique and the first of its kind.
- Connectivity
G+D also offers ‘out-of-the-box’ connectivity, optimised specifically for IoT applications. This covers over 600 mobile networks in 185 countries. Furthermore, even 3GPP-based satellite network connectivity can be offered in remote areas, meaning truly global coverage is achieved. - Connectivity and lifecycle management with IoT Suite
G+D’s IoT Suite is an innovative connectivity management platform that offers a new level of IoT management. This platform seamlessly integrates with SGP.32, ensuring maximum compatibility for IoT devices. Devices and accounts can be visualized and monitored from a single dashboard, which effortlessly integrates with existing systems, thanks to its open API and agnostic technology
Comment on this article via X: @IoTNow_










